Muddling Meerkat, a mysterious DNS Operation involving China’s Great Firewall
Security Affairs
MAY 1, 2024
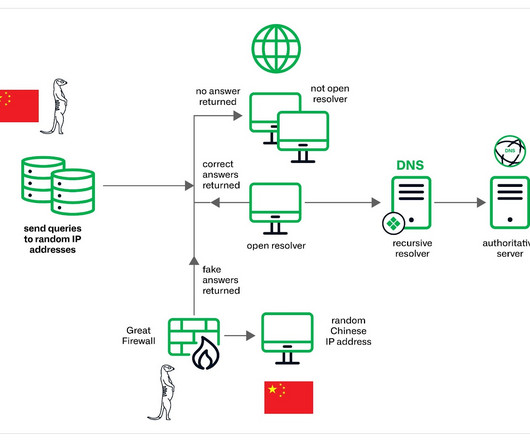
The China-linked threat actors Muddling Meerkat are manipulating DNS to probe networks globally since 2019. Infoblox researchers observed China-linked threat actors Muddling Meerkat using sophisticated DNS activities since 2019 to bypass traditional security measures and probe networks worldwide.



































Let's personalize your content