Mozi P2P Botnet also targets Netgear, Huawei, and ZTE devices
Security Affairs
AUGUST 20, 2021
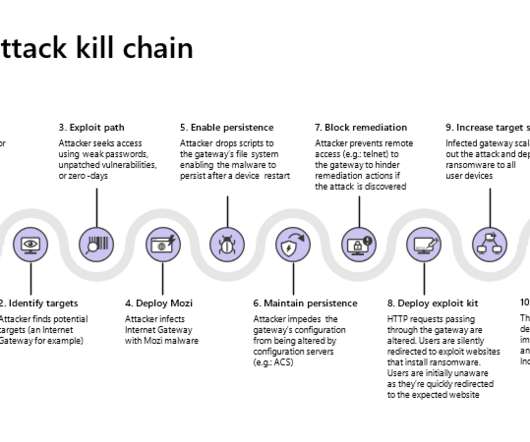
Microsoft researchers reported that the Mozi botnet was improved by implementing news capabilities to target network gateways manufactured by Netgear, Huawei, and ZTE. According to the researchers, in the last months of 2019, the botnet was mainly involved in DDoS attacks. Follow me on Twitter: @securityaffairs and Facebook.













Let's personalize your content