Borat RAT, a new RAT that performs ransomware and DDoS attacks
Security Affairs
APRIL 3, 2022
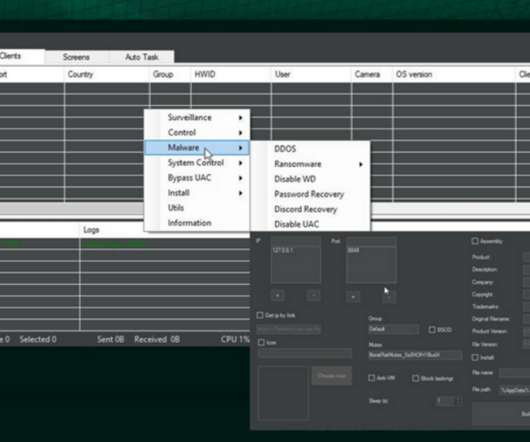
Cyble researchers discovered a new remote access trojan (RAT) named Borat capable of conducting DDoS and ransomware attacks. Unlike other RATs, the Borat RAT provides Ransomware and DDOS services to attackers expanding their capabilities. DDOS – This module is used to perform a DDOS attack. ” concludes Cyble.





























Let's personalize your content