Building a scalable RAVPN architecture in Oracle Cloud Infrastructure using Cisco Secure Firewall
Cisco Security
JULY 9, 2021
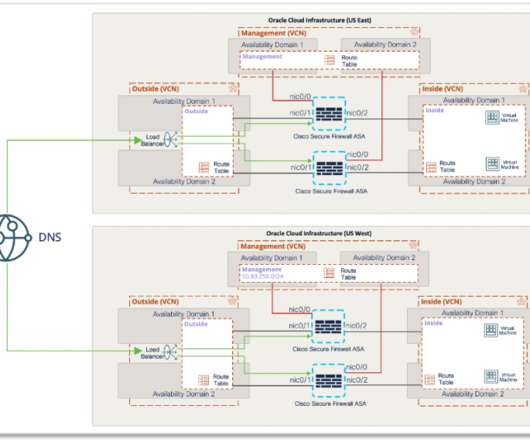
With Cisco Secure Firewall, organizations are able to build a scalable RAVPN architecture on OCI, providing employees secure remote access to their organization’s resources from any location or endpoint. It enforces security at the DNS layer to block malware, phishing, and command and control callbacks over any port.


































Let's personalize your content