Operation Spalax, an ongoing malware campaign targeting Colombian entities
Security Affairs
JANUARY 14, 2021
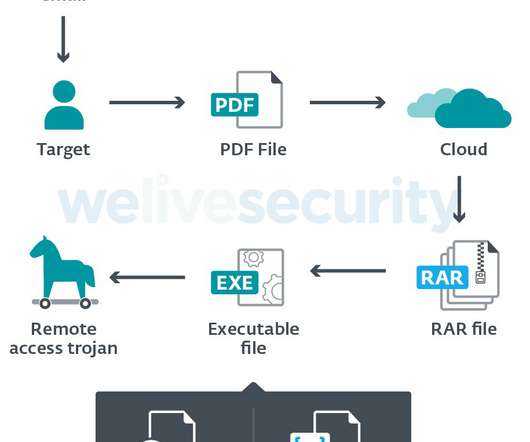
Security experts from ESET uncovered an ongoing surveillance campaign, dubbed Operation Spalax , against Colombian government institutions and private companies. Malware researchers from ESET uncovered an ongoing surveillance campaign, dubbed Operation Spalax , against Colombian entities exclusively. Pierluigi Paganini.













Let's personalize your content