Getting Over the DNS Security Awareness Gap
Dark Reading
JUNE 16, 2023
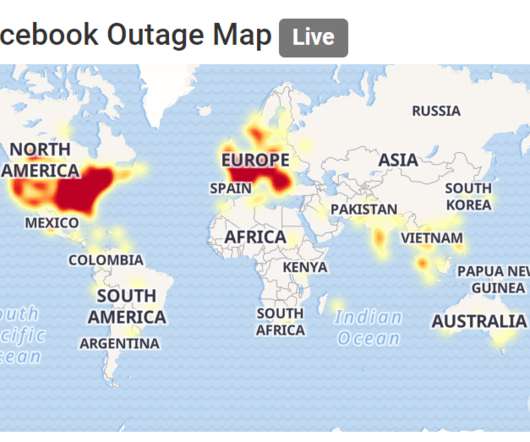
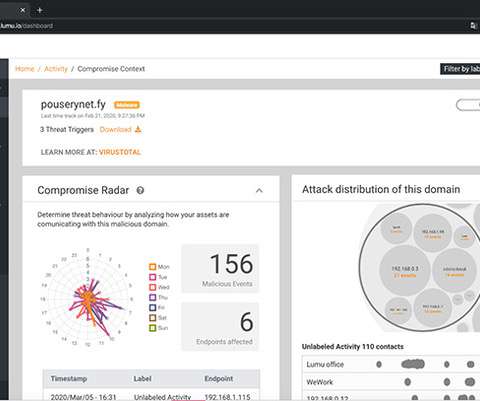
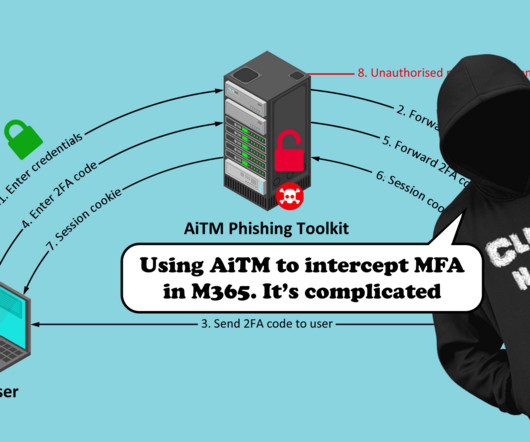
To properly secure DNS infrastructure, organizations need strong security hygiene around DNS infrastructure and records management as well as closely monitoring and filtering DNS traffic.









































Let's personalize your content