New DNS Spoofing Threat Puts Millions of Devices at Risk
eSecurity Planet
MAY 3, 2022
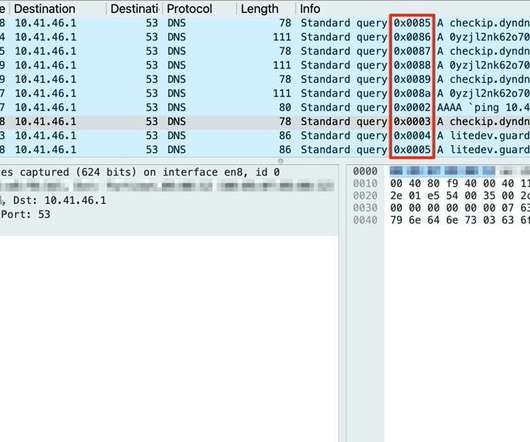
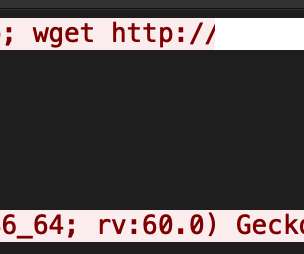
Security researchers have uncovered a critical vulnerability that could lead to DNS spoofing attacks in two popular C standard libraries that provide functions for common DNS operations. Understanding DNS Spoofing Attacks. For example, when you enter [link] the browser queries a DNS service to reach the matching servers.




















Let's personalize your content