North Korea-linked APT Emerald Sleet is using a new tactic
Security Affairs
FEBRUARY 12, 2025
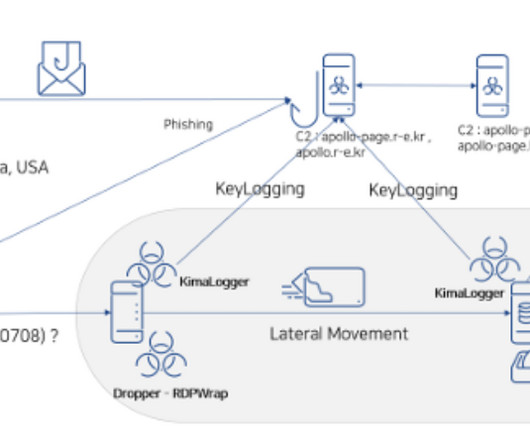
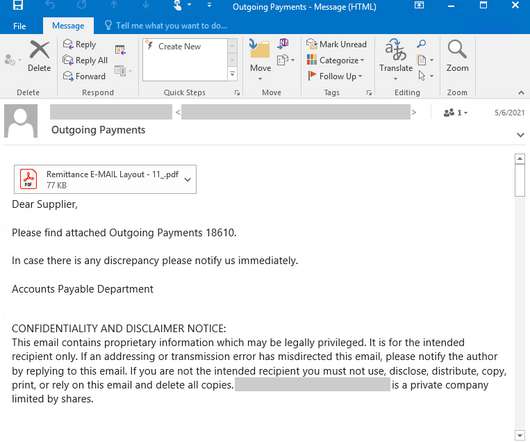
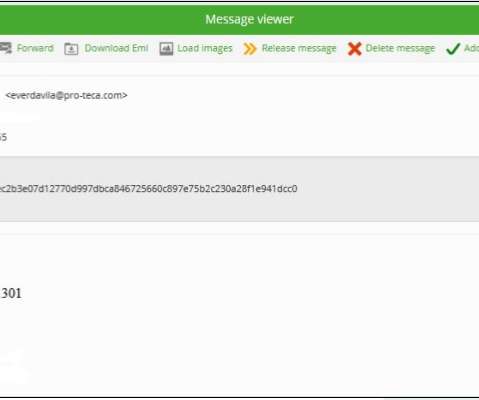
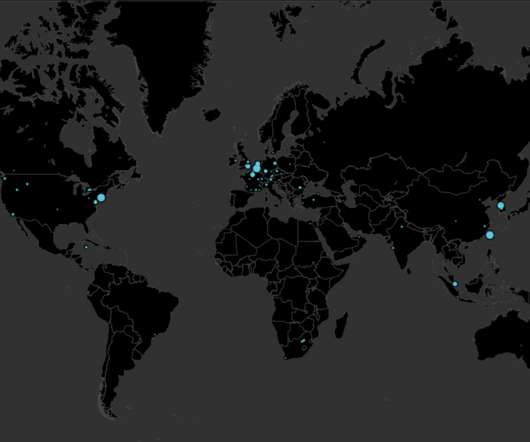
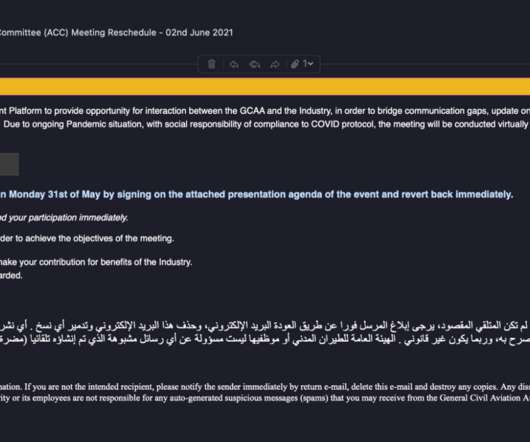
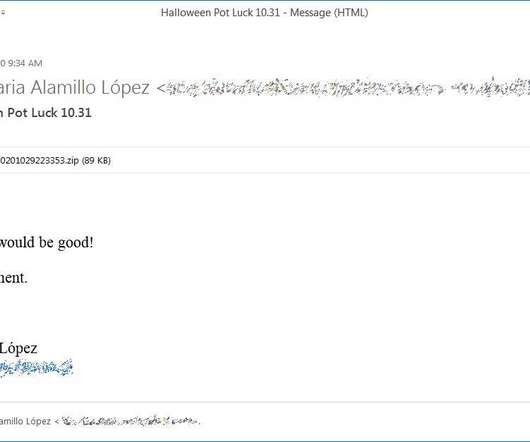
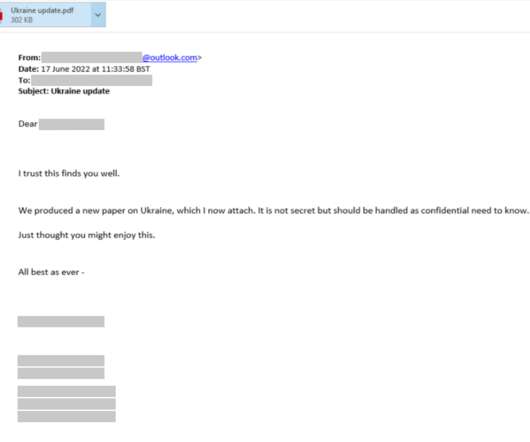
Recently, researchers from AhnLab Security Intelligence Center (ASEC) observed North Koreas Kimsuky APT group conducting spear-phishing attacks to deliver forceCopy info-stealer malware. LNK shortcut files, disguised as Office documents.























Let's personalize your content