GUEST ESSAY: Going beyond watermarks to protect sensitive documents from illegal access
The Last Watchdog
JANUARY 6, 2022
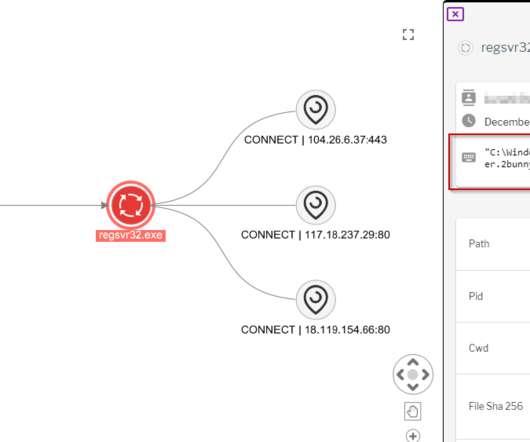
They also enrich documents with metadata and place them in crypto-containers, access to which is only granted by permission. However, all of these solutions are powerless when it comes to photographing a document with a smartphone and compromising printed copies of documents. There are more exotic ways of protecting documents.



































Let's personalize your content