RSAC insights: Concentric AI directs Google’s search techniques towards locking down data sprawl
The Last Watchdog
JUNE 1, 2022
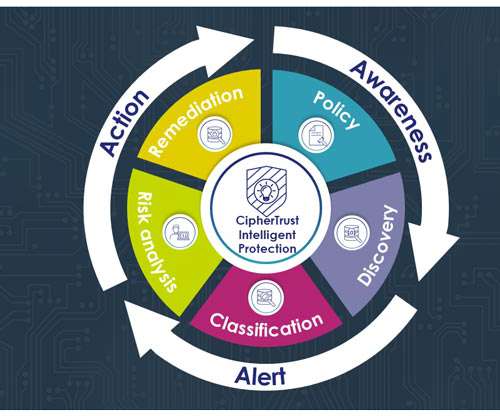
Security teams generally knew which on-premises server held certain batches of both structured and unstructured data; they could narrowly control access to a company’s on-premises data centers, and that was deemed good-enough, security-wise, he says.

















Let's personalize your content