OneTrust Enhances Data Discovery and Governance by Introducing AI-Powered Document Classification
Dark Reading
MAY 4, 2023
Organizations can effectively classify unstructured data, automatically apply policies, and remediate violations.

Dark Reading
MAY 4, 2023
Organizations can effectively classify unstructured data, automatically apply policies, and remediate violations.

Security Affairs
MARCH 8, 2024
The data exfiltrated by the gang included classified information and sensitive personal data from the Federal Administration. million files, and 65,000 documents were classified by NCSC as data relevant to the Federal Administration. Threat actors stole and leaked roughly 1.3 ” continues the report.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 3, 2022
Digital content creation is flourishing with intellectual property, financial records, marketing plans and legal documents circulating within a deeply interconnected digital ecosystem. The trend that we’re seeing is that more than 30 percent of the content flowing into data lakes is from untrusted sources,” he says. “It’s

Thales Cloud Protection & Licensing
DECEMBER 11, 2023
Part of this process includes identifying where and how data is stored—on-premises, in third-party servers or in the cloud. While an organization might already know the location of structured data such as a primary customer database store, unstructured data (such as that found in stray files and emails) is more difficult to locate.

Security Affairs
JULY 3, 2023
Examples: Customer Personal Identifiable Information, transactional data, inventory records, and financial statements. Unstructured Data: Unstructured data, on the other hand, is characterized by its lack of organization and predefined format. It contains elements of both organized and unorganized data.

Centraleyes
APRIL 8, 2024
Data governance management programs help demonstrate that your business has a sound risk management approach, which can lower your rates. Comprehensive Documentation and Audit Trails: Detailed documentation and audit trails provide evidence of compliance during regulatory audits.
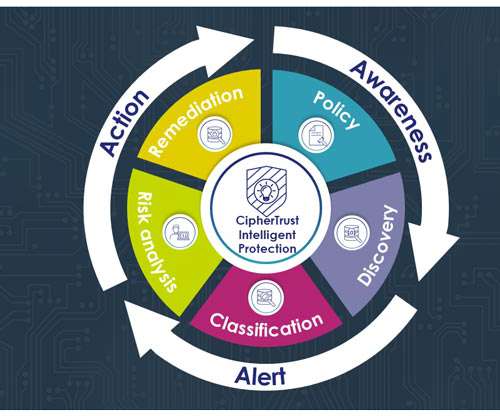
Thales Cloud Protection & Licensing
NOVEMBER 11, 2021
The volume of confidential documents created daily is, frankly, incalculable, and the volume of “everything” distributed across multiple data centers around the world is much, much more. The first step to Intelligent Data Protection is to find the sensitive data. Don't Encrypt Everything; Protect Intelligently.
Let's personalize your content