Lumma Stealer – Tracking distribution channels
SecureList
APRIL 21, 2025
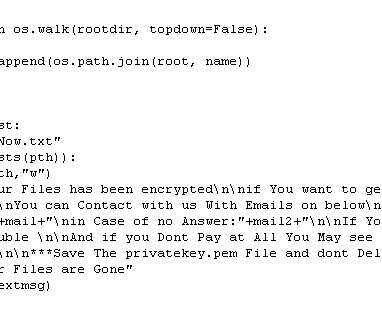
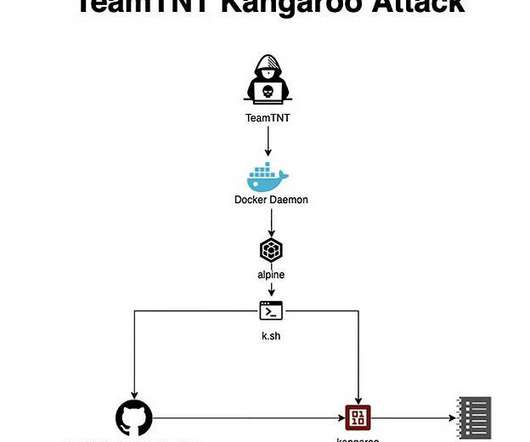
txt file contains aBase64-encoded PowerShell script that then downloads and runs theLumma Stealer. txt The script performs the following actions: Downloads the malware. It downloads the win15.zip The encrypted payload To decrypt the payload independently, we wrote a custom Python script that you can see in the screenshot below.














































Let's personalize your content