Risks to Your Network from Insecure Code Signing Processes
Security Boulevard
JULY 7, 2022
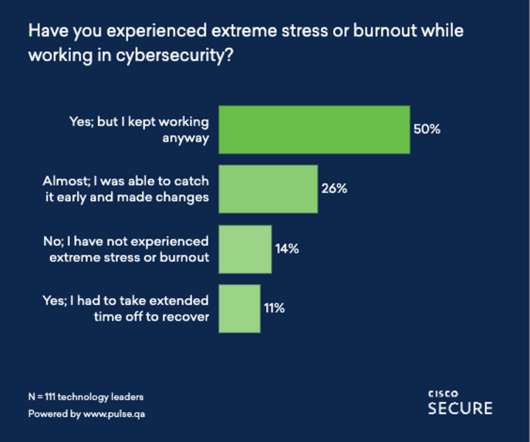
Many InfoSec teams don’t have the visibility into what their software development teams are doing. However, InfoSec teams need to understand that significant risks exist around poor code signing hygiene. In years past, InfoSec may have been the central keeper of code signing. Read our free eBook! "> Off. UTM Medium.















Let's personalize your content