Silent Ransom Group targeting law firms, the FBI warns
Security Affairs
MAY 24, 2025
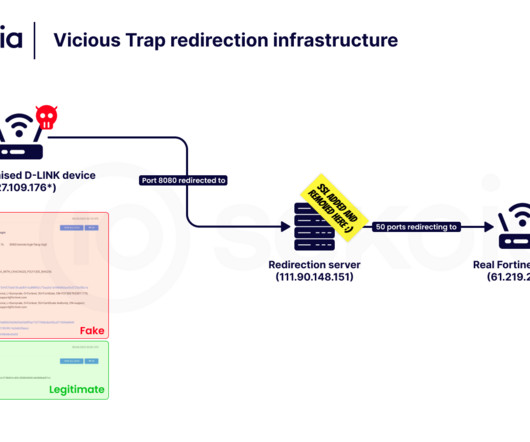
FBI warns Silent Ransom Group has targeted U.S. law firms for 2 years using callback phishing and social engineering extortion tactics. The FBI warns that the Silent Ransom Group, active since 2022 and also known as Luna Moth, has targeted U.S. law firms using phishing and social engineering. Linked to BazarCall campaigns, the group previously enabled Ryuk and Conti ransomware attacks. “The cyber threat actor Silent Ransom Group (SRG), also known as Luna Moth, Chatty Spider, and UNC3753, i








































Let's personalize your content