Akamai Report: LockBit, Cl0P Expand Ransomware Efforts
Tech Republic Security
AUGUST 19, 2023
Phishing is so last year: Akamai's report finds that zero-day and one-day vulnerabilities caused a 143% increase in total ransomware victims.

Tech Republic Security
AUGUST 19, 2023
Phishing is so last year: Akamai's report finds that zero-day and one-day vulnerabilities caused a 143% increase in total ransomware victims.
The Hacker News
AUGUST 19, 2023
Cybersecurity researchers have detailed an updated version of an advanced fingerprinting and redirection toolkit called WoofLocker that's engineered to conduct tech support scams.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
AUGUST 19, 2023
RMM tools are the easy targets for cyber attackers, and the related news over past year has highlighted several breaches initiated through RMM tools. The post CISA Releases Cyber Defense Plan For Remote Monitoring And Management (RMM) Software appeared first on Seceon. The post CISA Releases Cyber Defense Plan For Remote Monitoring And Management (RMM) Software appeared first on Security Boulevard.
Security Affairs
AUGUST 19, 2023
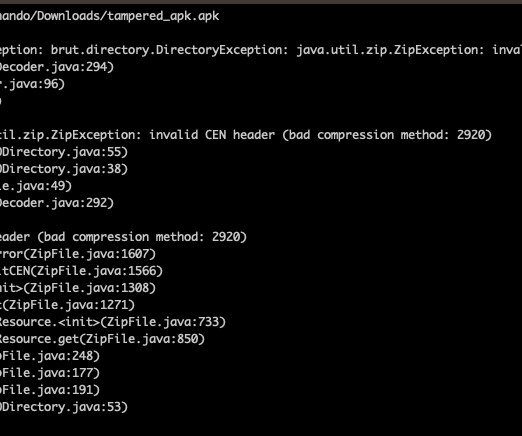
Threat actors are using Android Package (APK) files with unsupported compression methods to prevent malware analysis. On June 28th, researchers from Zimperium zLab researchers observed that Joe Sandbox announced the availability of an Android APK that could not be analyzed from most of the anti-decompilation tools. What is the best way to bypass #Malware analysis on #Android ?

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
AUGUST 19, 2023
The China-aligned APT (advanced persistent threat) group known as 'Bronze Starlight' was seen targeting the Southeast Asian gambling industry with malware signed using a valid certificate used by the Ivacy VPN provider. [.

The Hacker News
AUGUST 19, 2023
Networking hardware company Juniper Networks has released an "out-of-cycle" security update to address multiple flaws in the J-Web component of Junos OS that could be combined to achieve remote code execution on susceptible installations. The four vulnerabilities have a cumulative CVSS rating of 9.8, making them Critical in severity. They affect all versions of Junos OS on SRX and EX Series.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
AUGUST 19, 2023
Serde, a popular Rust (de)serialization project, has decided to ship its serde_derive macro as a precompiled binary. This has generated a fair amount of concern among some developers who highlight the future legal and technical issues this may pose, along with a potential for supply chain attacks. [.
DoublePulsar
AUGUST 19, 2023
With just weeks until the release of Bethesda’s next Han Solo role playing video game, threat actors are already queuing up trojan-ised versions of the game. Unearthed While on the hunt for malware, I came across this sample on Google’s VirusTotal, uploaded last week from a US IP address: Source: VirusTotal It’s notable for a bunch of reasons, including the fact it uses the legit Starfield logo: Source: my PC The executable name was also Starfield.exe on upload: The file itself is a remote acces
WIRED Threat Level
AUGUST 19, 2023
New research reveals the strategies hackers use to hide their malware distribution system, and companies are rushing to release mitigations for the “Downfall” processor vulnerability on Intel chips.
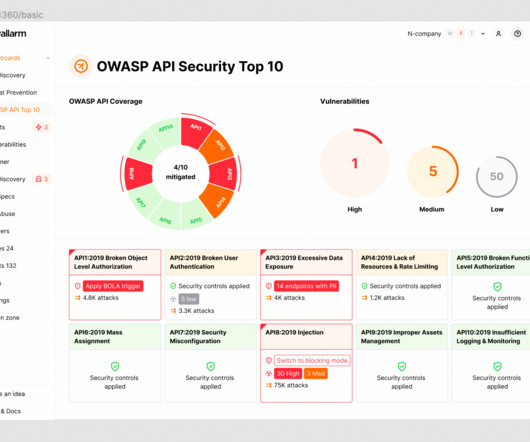
Security Boulevard
AUGUST 19, 2023
Welcome to the 5th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular focus on security practitioners. This post will focus on API4:2023 Unrestricted Resource Consumption. In this series we are taking an in-depth look at each category – the details, the impact and what you can [.] The post 2023 OWASP Top-10 Series: API4:2023 Unrestricted Resource Consumption appeared first on Wallarm.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Identity IQ
AUGUST 19, 2023
Debt Snowball or Debt Avalanche: Which Debt Repayment Method is Right for You? IdentityIQ Whether it’s personal loans, student loans, car payments, or credit card debt, people owe more money today than they ever have. If you’re one of the millions of people struggling to pay back loans and debts, you’ve come to the right place. This article explores two of the most common methods of debt repayment — the debt avalanche and the debt snowball.

Security Boulevard
AUGUST 19, 2023
Many thanks to BSidesTLV for publishing their presenter’s erudite BSidesTLV 2023 security content on the organizations’ YouTube channel. Permalink The post BSidesTLV 2023 – Ofir Balassiano & Ofir Shaty – The Dark Side Of Cloud-Based Database Engines appeared first on Security Boulevard.
Let's personalize your content