International Malware Takedown Seized 100+ Servers
Tech Republic Security
MAY 31, 2024
‘Operation Endgame’ is an ongoing, law enforcement effort to disrupt botnets, malware droppers and malware-as-a-service.

Tech Republic Security
MAY 31, 2024
‘Operation Endgame’ is an ongoing, law enforcement effort to disrupt botnets, malware droppers and malware-as-a-service.
The Hacker News
MAY 31, 2024
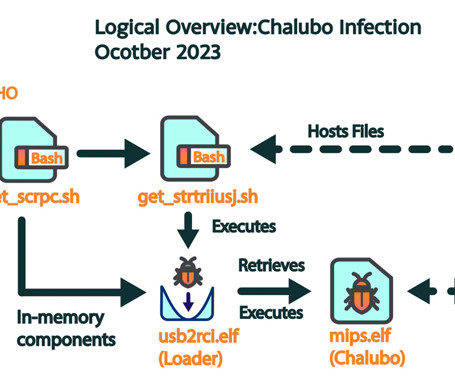
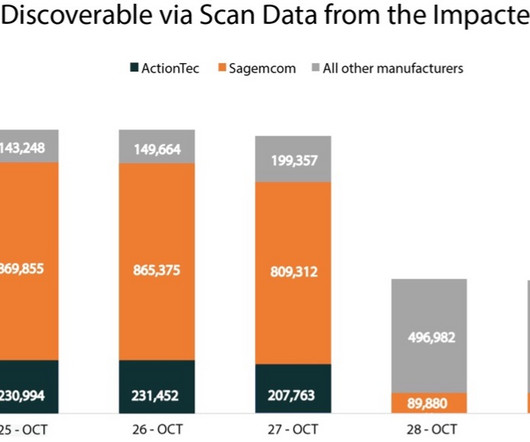
More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline following a destructive cyber attack staged by unidentified cyber actors, disrupting users' access to the internet. The mysterious event, which took place between October 25 and 27, 2023, and impacted a single internet service provider (ISP) in the U.S.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
MAY 31, 2024
The threat actor ShinyHunters claims breach of Santander and is offering for sale bank data, including information for 30 million customers. A notorious threat actor ShinyHunters is offering a huge trove of data allegedly stolen from the Santander Bank for sale. ShinyHunters claims to have stolen information for 30 million customers, employees, and bank account data.
The Hacker News
MAY 31, 2024
OpenAI on Thursday disclosed that it took steps to cut off five covert influence operations (IO) originating from China, Iran, Israel, and Russia that sought to abuse its artificial intelligence (AI) tools to manipulate public discourse or political outcomes online while obscuring their true identity.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Graham Cluley
MAY 31, 2024
US spyware vendor pcTattletale has shut down its operations following a serious data breach that exposed sensitive information about its customers, as well as data stolen from some of their victims. pcTattletale was promoted as "employee and child monitoring software" designed to "protect your business and family." Of course, what it actually was, was a way to surreptitiously spy upon other people's phones and computers - secretly viewing everything they did.
The Hacker News
MAY 31, 2024
The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
MAY 31, 2024
The Chalubo trojan destroyed over 600,000 SOHO routers from a single ISP, researchers from Lumen Technologies reported. Between October 25 and October 27, 2023, the Chalubo malware destroyed more than 600,000 small office/home office (SOHO) routers belonging to the same ISP. Black Lotus did not name the impacted ISP, however, Bleeping Computer speculates the attack is linked to the Windstream outage that occurred during the same timeframe.

Webroot
MAY 31, 2024
What is Internet Safety Month? Each June, the online safety community observes Internet Safety Month as a time to reflect on our digital habits and ensure we’re taking the best precautions to stay safe online. It serves as a reminder for everyone—parents, teachers, and kids alike—to be mindful of our online activities and to take steps to protect ourselves.

The Hacker News
MAY 31, 2024
Microsoft has emphasized the need for securing internet-exposed operational technology (OT) devices following a spate of cyber attacks targeting such environments since late 2023. "These repeated attacks against OT devices emphasize the crucial need to improve the security posture of OT devices and prevent critical systems from becoming easy targets," the Microsoft Threat Intelligence team said.
Penetration Testing
MAY 31, 2024
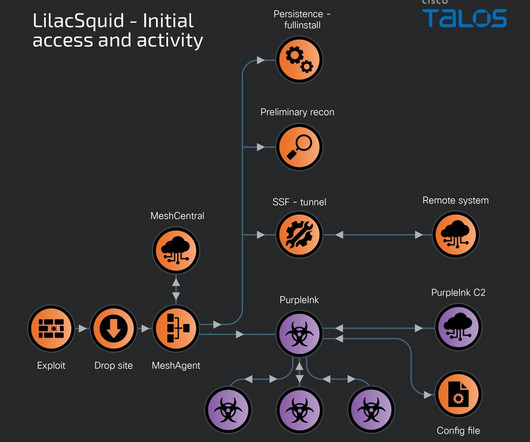
Cisco Talos, the threat intelligence and research arm of Cisco, has exposed a sophisticated espionage-focused threat actor known as LilacSquid (UAT-4820). This advanced persistent threat (APT) group has been operating under the radar since... The post LilacSquid APT Unveiled: A Stealthy Campaign Targeting Global Industries appeared first on Penetration Testing.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Bleeping Computer
MAY 31, 2024
A threat actor claiming recent Santander and Ticketmaster breaches says they stole data after hacking into an employee's account at cloud storage company Snowflake. However, Snowflake disputes these claims, saying recent breaches were caused by poorly secured customer accounts. [.
Cisco Security
MAY 31, 2024
OSIM is a great advancement towards a more secure and resilient supply chain ecosystem. OSIM is a great advancement towards a more secure and resilient supply chain ecosystem.

SecureWorld News
MAY 31, 2024
I ran across this fascinating post on ClearanceJobs, the largest career network for professionals with federal government security clearance, listing the " 10 Highest Paying Tech Jobs in 2024 and Beyond." What caught my eye were two things: 1) The number of these jobs that did not exist 10, five, or even one or two years ago; and 2) How many of the roles are tied to cybersecurity—directly or indirectly.

Malwarebytes
MAY 31, 2024
On May 29, 2024, the US Department of Justice (DOJ) announced it had dismantled what was likely the world’s largest botnet ever. This botnet, called “911 S5,” infected systems at over 19 million IP addresses across more than 190 countries. The main sources of income for the operators, who stole a billions of dollars across a decade, came from committing pandemic and unemployment fraud, and by selling access to child exploitation materials.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Bleeping Computer
MAY 31, 2024
Live Nation has confirmed that Ticketmaster suffered a data breach after its data was stolen from a third-party cloud database provider, which is believed to be Snowflake. [.

The Last Watchdog
MAY 31, 2024
AI has the potential to revolutionize industries and improve lives, but only if we can trust it to operate securely and ethically. Related: The key to the GenAI revolution By prioritizing security and responsibility in AI development, we can harness its power for good and create a safer, more unbiased future. Developing a secured AI system is essential because artificial intelligence is a transformative technology, expanding its capabilities and societal influence.

Quick Heal Antivirus
MAY 31, 2024
“Investment is subject to market risk please read the offer document carefully before investment”, we all have literally. The post Cyber Attacks Unpacked: Recent fraud Incidents and Impact (25th to 31st May, 2024) appeared first on Quick Heal Blog.

The Hacker News
MAY 31, 2024
Digital content is a double-edged sword, providing vast benefits while simultaneously posing significant threats to organizations across the globe. The sharing of digital content has increased significantly in recent years, mainly via email, digital documents, and chat.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Heimadal Security
MAY 31, 2024
Ticketmaster has been breached and the data of over 500 million customers is listed for sale. A threat actor known as ShinyHunters is selling on the recently revived BreachForums hacking forum what they claim is the personal and financial information of Ticketmaster customers. The listing goes for $500,000. Details About the Breach: What Information Was […] The post Ticketmaster Breached?

SecureBlitz
MAY 31, 2024
In this post, I will show you 4 ways technology can help your marketing efforts. In the rapidly evolving digital world, using technology in marketing campaigns is essential to success and is no longer optional. Businesses that want to remain ahead of the competition need to adopt cutting-edge techniques and products that not only grab […] The post 4 Ways Technology Can Help Your Marketing Efforts appeared first on SecureBlitz Cybersecurity.

Bleeping Computer
MAY 31, 2024
Europol and German law enforcement have revealed the identities of eight cybercriminals linked to the various malware droppers and loaders disrupted as part of the Operation Endgame law enforcement operation. [.
Penetration Testing
MAY 31, 2024
A new and sophisticated malware named AsukaStealer has emerged on the cybercrime scene, offering its malicious services for a surprisingly low monthly fee of $80. This C++ based malware, marketed on a Russian-language forum,... The post AsukaStealer Malware Targets Browsers and Crypto Wallets for $80 a Month appeared first on Penetration Testing.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
MAY 31, 2024
Japanese bitcoin exchange DMM Bitcoin is warning that 4,502.9 Bitcoin (BTC), or approximately $308 million (48.2 billion yen), has been stolen from one of its wallets today, making it the most significant cryptocurrency heist of 2024. [.

Digital Shadows
MAY 31, 2024
ReliaQuest reveals new ClearFake campaign tricks users into running malicious PowerShell. Learn to block IoCs, limit PowerShell, and educate users against this evolving threat.

Bleeping Computer
MAY 31, 2024
A threat actor known as ShinyHunters is claiming to be selling a massive trove of Santander Bank data, including information for 30 million customers, employees, and bank account data, two weeks after the bank reported a data breach. [.

We Live Security
MAY 31, 2024
A facial recognition system misidentifies a woman in London as a shoplifter, igniting fresh concerns over the technology's accuracy and reliability

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Zero Day
MAY 31, 2024
Powering off your phone regularly, disabling Bluetooth when it's not needed, and using only trusted accessories are just some of the NSA's security recommendations.

Heimadal Security
MAY 31, 2024
The BBC has revealed that on May 21, a data security breach resulted in unauthorized access to files held on a cloud-based service, jeopardizing the confidentiality of members of the BBC Pension Scheme. What Do We Know About the Incident? The incident impacted roughly 25,000 people according to the reports, including former and current employees […] The post BBC Breached!
Penetration Testing
MAY 31, 2024
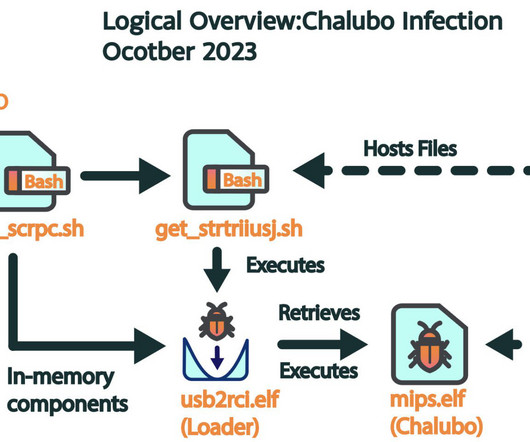
A destructive cyberattack, dubbed “The Pumpkin Eclipse” by Lumen Technologies’ Black Lotus Labs, has knocked out over 600,000 small office/home office (SOHO) routers, leaving a significant portion of an internet service provider’s (ISP) customers... The post Chalubo Malware Wreaks Havoc: Half a Million Routers Permanently Disabled appeared first on Penetration Testing.

BH Consulting
MAY 31, 2024
In 2023, the DPC was responsible for handling 87 per cent of all GDPR-related fines in Europe, totalling €1.55 billion. But with many of the largest cases undergoing appeals, the actual amount of fines paid was a fraction of that. In reality, the report shows that the amount paid to the Irish regulator was just €1.375 million. That’s just one of the many findings that caught my eye from the Data Protection Commission’s annual report for 2023.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content