Where Next for Quantum Computing and Cybersecurity?
Lohrman on Security
JULY 3, 2022
We’ve been hearing about upcoming breakthroughs with quantum computing technology for several years, so what’s the latest from around the world?
Lohrman on Security
JULY 3, 2022
We’ve been hearing about upcoming breakthroughs with quantum computing technology for several years, so what’s the latest from around the world?

CyberSecurity Insiders
JULY 3, 2022
In the year 2019, a Netherlands-based University was victimized by a ransomware attack where cyber criminals demanded 200,000 Euros or $200,000 in the BTC to free up the database from encryption. As the educational institution was about to lose valuable staff, students and curriculum related data, it bowed down to the demands of ransomware spreading gang/s.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Boulevard
JULY 3, 2022
We’ve been hearing about upcoming breakthroughs with quantum computing technology for several years, so what’s the latest from around the world? The post Where Next for Quantum Computing and Cybersecurity? appeared first on Security Boulevard.

CyberSecurity Insiders
JULY 3, 2022
A cyber gang has leaked data of thousands of British school pupils online and is also threatening to add more to the list, as almost all the 6 victims have chosen not to entertain the cyber criminals. Information is out that sensitive details such as passport numbers of children, their identity related documents, disciplinary statements, and child protection reports were accessed and stolen by hackers last month.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
JULY 3, 2022
Jenkins security team disclosed tens of flaws affecting 29 plugins for the Jenkins automation server, most of them are yet to be patched. Jenkins is the most popular open-source automation server, it is maintained by CloudBees and the Jenkins community. The automation server supports developers build, test and deploy their applications, it has hundreds of thousands of active installations worldwide with more than 1 million users.
Security Boulevard
JULY 3, 2022
What cyber threats the future brings to us? An analysis of the cybersecurity strategies of Canada, New Zealand, the UK, the US, and Australia. The post Five Eyes Cyber Security Predictions appeared first on Rainbow and Unicorn. The post Five Eyes Cyber Security Predictions appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
JULY 3, 2022
What is Mac Address? MAC Address is a permanent physical address. It is assigned by the device manufacturer and it was unique. An IP address is used to identify the device on the internet and a MAC address is used to identify the device between the multiple devices within the network and transfer the data […]. The post How to Change Mac Address in Linux – HackerNet appeared first on Security Boulevard.

Security Affairs
JULY 3, 2022
Google Project Zero states that in H1 2022 at least half of zero-day issues exploited in attacks were related to not properly fixed old flaws. Google Project Zero researcher Maddie Stone published a blog post that resumes her speech at the FIRST conference in June 2022, the presentation is titled “ 0-day In-the-Wild Exploitation in 2022…so far “ Stone revealed that nine out of 18 zero-day flaws detected and disclosed as exploited in-the-wild in 2022 are variants of previously patched vulne

The Hacker News
JULY 3, 2022
Vulnerability coordination and bug bounty platform HackerOne on Friday disclosed that a former employee at the firm improperly accessed security reports submitted to it for personal gain. "The person anonymously disclosed this vulnerability information outside the HackerOne platform with the goal of claiming additional bounties," it said.

Bleeping Computer
JULY 3, 2022
Kaspersky has launched a new information hub to help with their open-source stalkerware detection tool named TinyCheck, created in 2019 to help people detect if their devices are being monitored. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Acunetix
JULY 3, 2022
Imagine the following situation. You work as a cybersecurity manager for a company that owns the website www.example.com. One day, your sales department receives an email from an unknown individual. The sales department forwards it to you. The email has the following content: You example.com/login.php. Read more. The post 7 steps to avoid uncoordinated vulnerability disclosure appeared first on Acunetix.

Bleeping Computer
JULY 3, 2022
Microsoft has announced the introduction of a new Microsoft Defender for Endpoint (MDE) feature in public preview to help organizations detect weaknesses affecting Android and iOS devices in their enterprise networks. [.].

Security Affairs
JULY 3, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs for free in your email box. The role of Social Media in modern society – Social Media Day 22 interview Experts shared PoC exploit code for RCE in Zoho ManageEngine ADAudit Plus tool A ransomware attack forced publishing giant Macmillan to shuts down its systems SessionManager Backdoor employed in attacks on Microsoft IIS servers worldwide A long-running cryptomining campaign

The State of Security
JULY 3, 2022
The job of a CISO is one of constant change and unexpected challenges. One of the most energetic environments to govern is that of a university. Universities function not only as academic institutions, but also as research hubs, hosting both curious students, as well as notable scholars. This is an audience not known for slow-motion […]… Read More.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Trend Micro
JULY 3, 2022
In this three-part blog series, we’ll look into Data Distribution Service, why it is critical, and how you can mitigate risks associated with it.

The State of Security
JULY 3, 2022
The widespread adaptability and integration of tools and the professionals who can effectively use them to comply with the law will significantly impact the careers of both lawyers and other legal personnel. One of the fastest-growing areas in the legal profession in the United States is Privacy Law. Privacy certifications endorse attorneys as credentialed privacy […]… Read More.
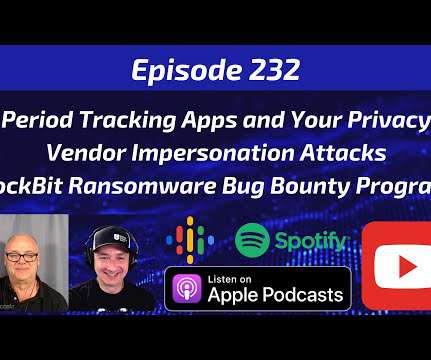
Security Boulevard
JULY 3, 2022
Period tracker apps are causing privacy concerns because they could potentially be used against women in states that ban abortion, new research shows that vendors are being impersonated more than employees in Business Email Compromise (BEC) attacks, and details on the first ever bug bounty program from the creators of the LockBit ransomware operation. ** […].

Errata Security
JULY 3, 2022
In this blogpost, I describe the Synology DS620slim. Mostly these are notes for myself, so when I need to replace something in the future, I can remember how I built the system. It's a "NAS" (network attached storage) server that has six hot-swappable bays for 2.5 inch laptop drives. That's right, laptop 2.5 inch drives. It makes this a tiny server that you can hold in your hand.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
JULY 3, 2022
Imagine the following situation. You work as a cybersecurity manager for a company that owns the website www.example.com. One day, your sales department receives an email from an unknown individual. The sales department forwards it to you. The email has the following content: You example.com/login.php. Read more. The post 7 steps to avoid uncoordinated vulnerability disclosure appeared first on Acunetix.

Bleeping Computer
JULY 3, 2022
The Privacy Protection Authority in Israel seized servers hosting multiple travel booking websites because their operator failed to address security issues that enabled data breaches affecting more than 300,000 individuals. [.].
Security Boulevard
JULY 3, 2022
The job of a CISO is one of constant change and unexpected challenges. One of the most energetic environments to govern is that of a university. Universities function not only as academic institutions, but also as research hubs, hosting both curious students, as well as notable scholars. This is an audience not known for slow-motion […]… Read More.

Security Boulevard
JULY 3, 2022
The widespread adaptability and integration of tools and the professionals who can effectively use them to comply with the law will significantly impact the careers of both lawyers and other legal personnel. One of the fastest-growing areas in the legal profession in the United States is Privacy Law. Privacy certifications endorse attorneys as credentialed privacy […]… Read More.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.
Security Boulevard
JULY 3, 2022
via the tremendous observational humor and satirical skillseta of Eugen Erhan (Illustrator) & Tudor Muscalu (Writer) at Fredo & Pid’jin™. Permalink. The post Fredo & Pid’jin™ ‘Don’t Install That’ appeared first on Security Boulevard.

Security Boulevard
JULY 3, 2022
Our sincere thanks to Security BSides Athens for publishing their Presenter’s Security BSides Athens 2022 Conference content on the organization’s’ YouTube channel. Permalink. The post Security BSides Athens 2022 – Nikolaos Vourdas’ ‘Talk 4 – COM HIJACKING VOODOO’ appeared first on Security Boulevard.

Security Boulevard
JULY 3, 2022
Our sincere thanks to Security BSides Athens for publishing their Presenter’s Security BSides Athens 2022 Conference content on the organization’s’ YouTube channel. Permalink. The post Security BSides Athens 2022 – Kiriaki Solomidou’s, John Torakis’ And George Tsigourakos’ ‘Talk 3 – Tales From The DevSecOps World.

Security Boulevard
JULY 3, 2022
In this blogpost, I describe the Synology DS620slim. Mostly these are notes for myself, so when I need to replace something in the future, I can remember how I built the system. It's a "NAS" (network attached storage) server that has six hot-swappable bays for 2.5 inch laptop drives. That's right, laptop 2.5 inch drives. It makes this a tiny server that you can hold in your hand.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Let's personalize your content