Cisco ASA vulnerability actively exploited after exploit released
Bleeping Computer
JUNE 27, 2021
Hackers are scanning for and actively exploiting a vulnerability in Cisco ASA devices after a PoC exploit was published on Twitter. [.].

Bleeping Computer
JUNE 27, 2021
Hackers are scanning for and actively exploiting a vulnerability in Cisco ASA devices after a PoC exploit was published on Twitter. [.].

Security Affairs
JUNE 27, 2021
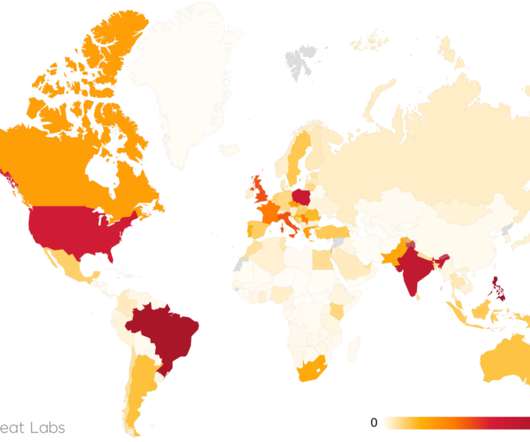
Experts warn of attacks against Cisco ASA devices after researchers have published a PoC exploit code on Twitter for a known XSS vulnerability. Experts warn of attacks against Cisco ASA devices after researchers from Positive Technologies have published a PoC exploit code on Twitter for the CVE-2020-3580 XSS vulnerability. PoC for XSS in Cisco ASA (CVE-2020-3580) POST /+CSCOE+/saml/sp/acs?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
JUNE 27, 2021
In yet another sign that the Russian hackers who breached SolarWinds network monitoring software to compromise a slew of entities never really went away, Microsoft said the threat actor behind the malicious cyber activities used password spraying and brute-force attacks in an attempt to guess passwords and gain access to its customer accounts.
Security Affairs
JUNE 27, 2021
Researchers have discovered a strain of cryptocurrency-mining malware, tracked as Crackonosh, that abuses Windows Safe mode to avoid detection. . Researchers from Avast have spotted a strain of cryptocurrency miner, tracked as Crackonosh, that abuses Windows Safe mode to avoid detection. “While the Windows system is in safe mode antivirus software doesn’t work.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
JUNE 27, 2021
As it turns out, native Windows apps are also getting a major redesign as part of the new operating system. The new look for native apps was highlighted during the event video and there's a chance we might see these new apps in the upcoming preview builds. [.].
The Hacker News
JUNE 27, 2021
A security vulnerability in Cisco Adaptive Security Appliance (ASA) that was addressed by the company last October and again earlier this April, has been subjected to active in-the-wild attacks following the release of proof-of-concept (PoC) exploit code.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CyberSecurity Insiders
JUNE 27, 2021
Amazon Web Services, a business unit of Amazon Cloud, has made it official that it is going to acquire Wickr that offers encrypted communication certified by National Security Agency. The financial details of the deal are yet to be known. But the deal is likely to complete by October 2021, provided all terms and conditions comply with the SEC stipulations. .
Security Affairs
JUNE 27, 2021
Researchers discovered six rogue packages in the official Python programming language’s PyPI repository containg cryptocurrency mining malware. Experts from security firm Sonatype have uncovered six typosquatting packages in the official Python programming language’s PyPI repository that were laced with cryptomining malware. The Python Package Index (PyPI) is a repository of software for the Python programming language, it allows users to easily find and install software developed and shared the

WIRED Threat Level
JUNE 27, 2021
As useful as all those add-ons can be, don't get complacent when it comes to making sure they're also secure.

Security Affairs
JUNE 27, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. Norway blames China-linked APT31 for 2018 government hack Poland: The leader of the PiS party blames Russia for the recent attack This bug can permanently break iPhone WiFi connectivity MI5 seized Boris Johnsons phone over security risk fears NSA releases guidance for

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
JUNE 27, 2021
While the entire anti-lockdown protesters in London are demanding the arrest of Matt Hancock, the health secretary; for breaching COVID lockdown rules and embracing & kissing his personal aide Gina Coladangelo, new speculation is doing rounds on the internet. . . Some Facebook groups are buzzing with speculation that the office romance caught in between Britain’s health secretary and his colleague Gina resulted from a footage leak from a Chinese covert camera that was fixed inside a light f

Trend Micro
JUNE 27, 2021
Follow the story of Company X as they suffer an attack from the notorious modern ransomware family, Nefilim, and their affiliates, to learn how you can better mitigate against the common tactic and techniques used in these attacks.

Bleeping Computer
JUNE 27, 2021
As it turns out, native Windows apps are also getting a major redesign as part of the new operating system. The new look for native apps was highlighted during the event video and there's a chance we might see these new apps in the upcoming preview builds. [.].

SecureBlitz
JUNE 27, 2021
Here, I will show you the top 5 benefits of using outsourcing services. If you are running a business yourself or you have a few employees, it can be quite overwhelming. You may end up not giving your business the full attention it needs to grow. This is where outsourcing comes in. With outsourcing, you. The post The Top 5 Benefits Of Using Outsourcing Services appeared first on SecureBlitz Cybersecurity.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Trend Micro
JUNE 27, 2021
Let's Talk Security: Season 02 // Episode 02: Host, Rik Ferguson, interviews Forrester Analyst, Allie Mellen. Together they discuss to adapt or die.

CyberSecurity Insiders
JUNE 27, 2021
The current model for cybersecurity is broken. It consists of acquiring and deploying a lot of stand-alone tools, each with its own console, to analyze logs or traffic and detect anomalies that could be threats. In this model, it’s up to each security analyst to communicate with other analysts to determine whether each tool’s individual detection (each of which, by itself, may look benign), can correlate with other detections from other tools to reveal a complex attack.

SecureBlitz
JUNE 27, 2021
Over 90,000 brute force attacks are made on WordPress websites every single minute. That’s insane! Isn’t it? That’s why it’s highly necessary to worry about the security of your WordPress. Owners of tiny websites may believe that their websites are not worth hacking. In fact, because small websites don’t prioritize security, it is all the. The post The Ultimate WordPress Security Guide For 2021 appeared first on SecureBlitz Cybersecurity.
Security Boulevard
JUNE 27, 2021
Last week, the world’s major democratic governments took steps to coordinate cybersecurity defenses, with the European Union and the United States launching an initiative to combat ransomware, which has become an increasingly critical national security issue. The stated goals of the partnership highlight law enforcement action, raising public awareness on how to protect networks as.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Let's personalize your content