Fooling a Voice Authentication System with an AI-Generated Voice
Schneier on Security
MARCH 1, 2023
A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.

Schneier on Security
MARCH 1, 2023
A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.
Jane Frankland
MARCH 1, 2023
Around the world, people are gearing up to celebrate International Women’s Day on 8 March. But I have to ask the difficult question/s. Is it really something worth celebrating in cybersecurity? Have we really made enough progress that’s worthy of a celebration? Let’s be honest. Many believe the answer is no, and that we should be striking or boycotting the day instead.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CSO Magazine
MARCH 1, 2023
In 2022, I started a podcast aimed at converting more Gen Z to seek careers in cybersecurity. In doing so, I had to educate myself on what they value and realized the many differences between Gen Z and previous generations. Gen Z refers to those born between mid-to-late 1990s and 2010, making them between the ages of 11 and 28. This means they grew up experiencing a much faster rate in which technology evolves.

Bleeping Computer
MARCH 1, 2023
Aruba Networks published a security advisory to inform customers about six critical-severity vulnerabilities impacting multiple versions of ArubaOS, its proprietary network operating system. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
MARCH 1, 2023
Software supply chain issues continue to be a concerning subject of late. Open source software (OSS) has many benefits, yet relying on many open source dependencies could cause security woes if it isn’t managed correctly. This problem has come into focus as more vulnerabilities present themselves and attacks on open source software ecosystems become more.
Bleeping Computer
MARCH 1, 2023
Microsoft has added two new utilities to the open-source PowerToys toolset to help Windows users paste text without formatting and make it easier to move the mouse across multiple screens or on ultra-wide monitors. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MARCH 1, 2023
Cisco has addressed a critical security vulnerability found in the Web UI of multiple IP Phone models that unauthenticated and remote attackers can exploit in remote code execution (RCE) attacks. [.

Security Boulevard
MARCH 1, 2023
Organizations worldwide store 60% of their data in the cloud. The popularity of cloud computing is undisputed in 2023 and is predicted to grow in future years. The main benefits of using cloud storage and computing services to run corporate virtual machines (VMs) include data availability and the cost-efficiency of such infrastructures. However, focusing on.

IT Security Guru
MARCH 1, 2023
Mobile phishing is an issue plaguing the masses and a growing concern for enterprises, particularly as 2022 had the highest percentage of mobile phishing encounter rates ever, according to Lookout ‘s Global State of Mobile Phishing report. On average, more than 30% of personal and enterprise users exposed to these attacks every quarter. In the U.K., there was a 35% increase in the average number of mobile devices exposed to at least one malicious phishing attack per quarter between 2020 a

Bleeping Computer
MARCH 1, 2023
When attempting to access Twitter's website, users see "Welcome to Twitter!" on the timeline. The alert, typically used for new signups, says, "Twitter is the best place to see what's happening in your world", with a Let's go button that lets you follow some people and topics. [.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CSO Magazine
MARCH 1, 2023
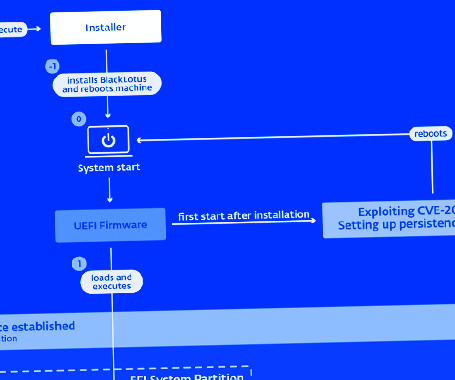
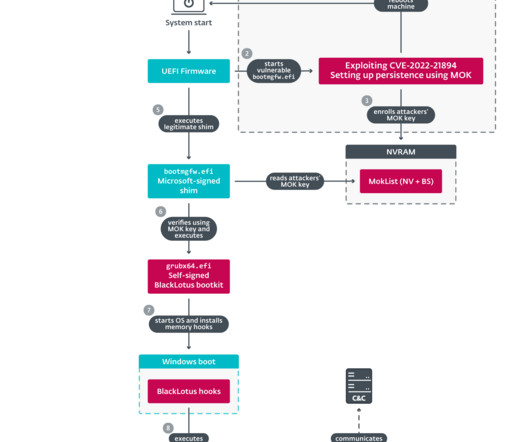
A Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus is found to be capable of bypassing an essential platform security feature, UEFI Secure Boot , according to researchers from Slovakia-based cybersecurity firm ESET. BlackLotus uses an old vulnerability and can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled, the researchers found.

Bleeping Computer
MARCH 1, 2023
Microsoft is investigating an ongoing outage that is blocking Exchange Online customers worldwide from accessing their mailboxes via any connection method or sending/receiving emails. [.
The Hacker News
MARCH 1, 2023
A stealthy Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.

Security Boulevard
MARCH 1, 2023
Federal agencies have 30 days to remove the popular Chinese social media app TikTok from federal government devices, according to a guidance memorandum issued by the White House. The memo, written by Office of Management and Budget director Shalanda Young and first seen and reported on by Reuters, applies to all federal agencies as well. The post White House Bans TikTok on Federal Devices appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

CyberSecurity Insiders
MARCH 1, 2023
From early this year, two malware variants targeted almost 6-7 law firms spread through two separate incidents, alerting whole of the world about the lurking cyber threat. Cybersecurity firm eSentire was the first to uncover the truth as its security analysts discovered that the two malicious software named GootLoader and SoCGholish were only infecting the servers used by employees of reputed law firms.

Dark Reading
MARCH 1, 2023
The flaw, which drew attention in October when it was found in ConnectWise products, could pose a significant risk to the supply chain if not patched immediately.

Bleeping Computer
MARCH 1, 2023
GitHub has announced that its secret scanning alerts service is now generally available to all public repositories and can be enabled to detect leaked secrets across an entire publishing history. [.

Security Boulevard
MARCH 1, 2023
LastPass has followed news of last month’s breach with details on a second attack in which developers were phished for their credentials. In the January incident, the password manager’s parent, GoTo, said that in addition to stealing encrypted backups containing customer data, hackers nicked an encryption key last November. “An unauthorized party gained access to.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
MARCH 1, 2023
The APT27 hacking group, aka "Iron Tiger," has prepared a new Linux version of its SysUpdate custom remote access malware, allowing the Chinese cyberespionage group to target more services used in the enterprise. [.

Malwarebytes
MARCH 1, 2023
Voice ID is slowly rolling out across various banks worldwide as a way to perform user authentication over the phone. However, questions remain about just how secure it is. Now that we have freely available artificial intelligence (AI) happily replicating people’s voices, could it be a security risk? Some recent research suggests that it could.

The Hacker News
MARCH 1, 2023
Cisco on Wednesday rolled out security updates to address a critical flaw impacting its IP Phone 6800, 7800, 7900, and 8800 Series products. The vulnerability, tracked as CVE-2023-20078, is rated 9.8 out of 10 on the CVSS scoring system and is described as a command injection bug in the web-based management interface arising due to insufficient validation of user-supplied input.
Security Affairs
MARCH 1, 2023
ESET discovered a stealthy Unified Extensible Firmware Interface (UEFI) bootkit dubbed BlackLotus that is able to bypass the Secure Boot on Windows 11. Researchers from ESET discovered a new stealthy Unified Extensible Firmware Interface ( UEFI ) bootkit, named BlackLotus , that is able to bypass Secure Boot on Windows 11. Secure Boot is a security feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 designed to detect tampering with boot loaders, key operating system files,

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

The Hacker News
MARCH 1, 2023
Google has announced the general availability of client-side encryption (CSE) for Gmail and Calendar, months after piloting the feature in late 2022. The data privacy controls enable "even more organizations to become arbiters of their own data and the sole party deciding who has access to it," Google's Ganesh Chilakapati and Andy Wen said.

Malwarebytes
MARCH 1, 2023
Despite a very slim browser market share, Internet Explorer (IE) is still being exploited by exploit kits like the RIG exploit kit (EK). One major advantage for the malware distributors behind the exploit kit is that the outdated browser has reached end-of-life (EOL), which means it no longer receives security updates and patches against known threats.

The Hacker News
MARCH 1, 2023
Six different law firms were targeted in January and February 2023 as part of two disparate threat campaigns distributing GootLoader and FakeUpdates (aka SocGholish) malware strains. GootLoader, active since late 2020, is a first-stage downloader that's capable of delivering a wide range of secondary payloads such as Cobalt Strike and ransomware.

Heimadal Security
MARCH 1, 2023
As a result of another attack on LastPass’s systems, the company disclosed a severe data breach in December 2022 that allowed threat actors to access encrypted password vaults. DevOps engineers’ home computers were breached and infected with a keylogger as part of a sustained cyber attack that exfiltrated sensitive data from Amazon AWS’s cloud storage […] The post LastPass Confirms Second Data Breach of Encrypted Password Vaults appeared first on Heimdal Security Blog.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Security Affairs
MARCH 1, 2023
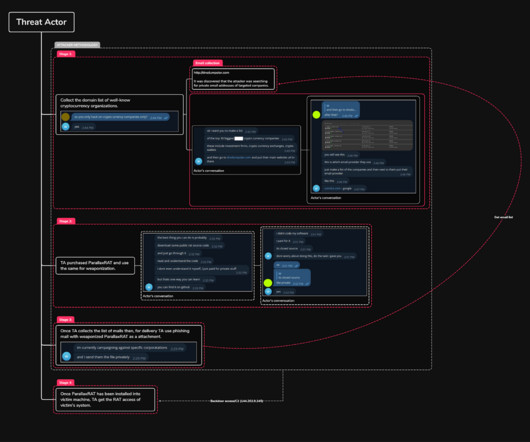
Experts warn of a new wave of attacks against cryptocurrency entities, threat actors are using a RAT dubbed Parallax RAT for Infiltration. Researchers from cybersecurity firm Uptycs warns of attacks targeting cryptocurrency organizations with the Parallax remote access Trojan (RAT). Parallax RAT has been distributed through malvertising and phishing campaigns since December 2019.

Bleeping Computer
MARCH 1, 2023
An ongoing phishing campaign is pretending to be Trezor data breach notifications attempting to steal a target's cryptocurrency wallet and its assets. [.

CompTIA on Cybersecurity
MARCH 1, 2023
Vlad Serov, a high school senior, has already earned five CompTIA certifications. See how his high school’s Cyber Lab program set him up for success.

Bleeping Computer
MARCH 1, 2023
Russia's internet watchdog agency Roskomnadzor is warning that today is the first day that laws banning the use of many foreign private messaging applications in the country come into force. [.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content