Donot Team cyberespionage group updates its Windows malware framework
Security Affairs
AUGUST 21, 2022
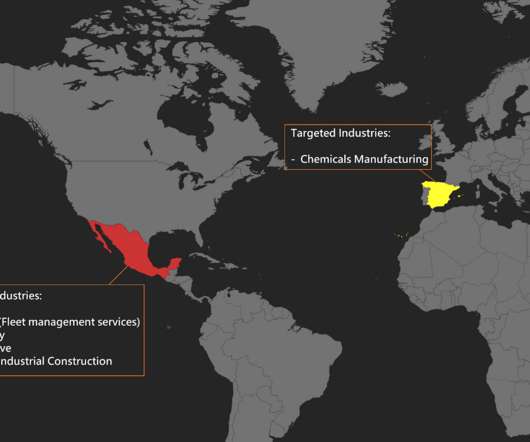
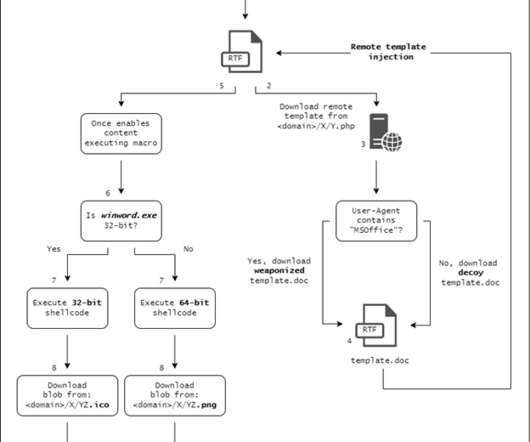
The Donot Team threat actor, aka APT-C-35 , has added new capabilities to its Jaca Windows malware framework. The Donot Team has been active since 2016, it focuses on government and military organizations, ministries of foreign affairs, and embassies in India, Pakistan, Sri Lanka, Bangladesh, and other South Asian countries. In October 2021, a report released by the Amnesty International revealed that the Donot Team group employed Android applications posing as secure chat application and mali




























Let's personalize your content