A Complete Guide to Watering Hole Attacks
Security Boulevard
SEPTEMBER 11, 2021
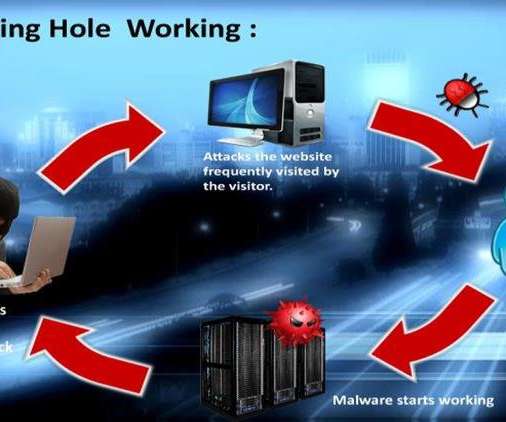
Watering Hole Attack: The Attack Vector Used In Targeting Florida Water Utilities! Do you know that no less than 1,000 end-user computers visited the site infected by the attackers during the 58-day window! But what are these attacks and how do they affect an organization? Well, this blog sums it all! Cyber criminals keep coming […]. The post A Complete Guide to Watering Hole Attacks appeared first on Kratikal Blogs.



















Let's personalize your content