Roseville, Calif., CIO Brings Global Background to Local Gov
Lohrman on Security
MARCH 19, 2023
Hong Sae is the CIO for the city of Roseville, Calif., and he has a tremendous track record of success in both Texas and California local government.

Lohrman on Security
MARCH 19, 2023
Hong Sae is the CIO for the city of Roseville, Calif., and he has a tremendous track record of success in both Texas and California local government.

Tech Republic Security
MARCH 19, 2023
PURPOSE The purpose of this Security Response Policy from TechRepublic Premium is to outline the security incident response processes which must be followed. This policy will assist to identify and resolve information security incidents quickly and effectively, thus minimizing their business impact and reducing the risk of similar incidents recurring.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MARCH 19, 2023
After the release of ChatGPT in November 2022, the OpenAI CEO and the people behind the conversational chatbot launch say that they are equally scared of the negative consequences that the newly developed technology can fetch in the future. Sam Altman, the tech brain leading the company, now owned by Microsoft, spoke a few words about what the world was intending to say about the tech.

Security Affairs
MARCH 19, 2023
The NBA (National Basketball Association) disclosed a data breach after a third-party firm providing a newsletter service was breached. The NBA (National Basketball Association) is notifying followers of a data breach after a third-party company providing a newsletter service was breached. The National Basketball Association (NBA) is a professional basketball league in Northern America composed of 30 teams (29 in the United States and 1 in Canada).

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

The Hacker News
MARCH 19, 2023
The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a potent and resilient threat despite attempts by law enforcement to take it down.
Security Affairs
MARCH 19, 2023
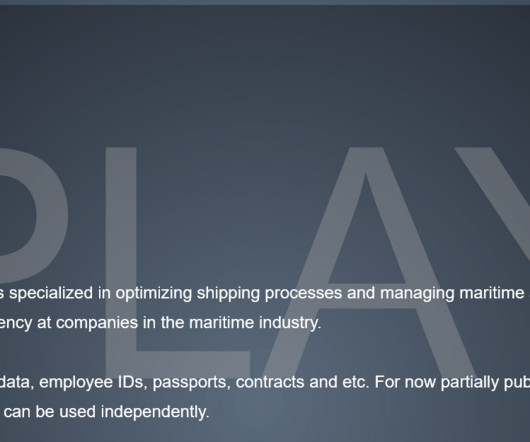
Dutch maritime logistics company Royal Dirkzwager suffered a ransomware attack, the company was hit by the Play ransomware gang. The Play ransomware group hit the Dutch maritime logistics company Royal Dirkzwager. Royal Dirkzwager is specialized in optimizing shipping processes and managing maritime and logistic information flows. The ransomware group added the company to its Tor data leak site and announced the theft of stolen private and personal confidential data, employee IDs, passports, con
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
MARCH 19, 2023
A misconfiguration on a website owned by the US-based Lowe’s Market grocery store chain could have allowed threat actors to gain control of its systems. On February 7, the Cybernews research team discovered a misconfiguration on the Lowe’s Market website. The supermarket chain’s website was leaking a treasure trove of private credentials, which left the company vulnerable to potential attacks by cybercriminals.

Bleeping Computer
MARCH 19, 2023
A new malware botnet was discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit devices into DDoS (distributed denial of service) swarm with the potential for massive attacks. [.

Security Affairs
MARCH 19, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Kaspersky released a new decryptor for Conti-based ransomware US govt agencies released a joint alert on the Lockbit 3.0 ransomware Feds arrested Pompompurin, the alleged owner of BreachForums Hitachi Energy breached by Clop gang through GoAnyw

WIRED Threat Level
MARCH 19, 2023
Open source intelligence researchers are verifying and debunking opaque claims about who ruptured the gas pipelines in the Baltic Sea.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Malwarebytes
MARCH 19, 2023
If you’ve ever downloaded software onto your computer, chances are you’ve unknowingly cluttered your machine with PUPs. Here’s what you need to know about these sneaky programs. What are PUPs? If you're thinking baskets of doe-eyed baby dogs, then you're sadly mistaken. PUPs is the acronym for Potentially Unwanted Programs. Also called bundleware, junkware, or PUAs (Potentially Unwanted Applications), PUPs are software programs that you likely didn't want installed on your comp

Trend Micro
MARCH 19, 2023
This article focuses on the healthcare sector. Over the past two years, the healthcare sector has been in a constant state of emergency due to the COVID-19 pandemic, and as widely reported in the media, it has also been threatened by cyberattacks such as ransomware.

Malwarebytes
MARCH 19, 2023
Last week on Malwarebytes Labs: "Brad Pitt," a still body, ketchup, and a knife, or the best trick ever played on a romance scammer, with Becky Holmes: Lock and Code S04E06 Breast cancer photos published by ransomware gang WhatsApp refuses to weaken encryption, would rather leave UK "Just awful" experiment points suicidal teens at chatbot Investment fraud overtakes business email compromise as most reported fraud Clop ransomware is victimizing GoAnywhere MFT customers Update now!

Security Boulevard
MARCH 19, 2023
In today’s digital world, identity theft and fraud have become increasingly common occurrences. It is no secret that fraudsters are getting more creative, making it more challenging for businesses and individuals to protect themselves. However, with the advent of technology, there are various ways to mitigate these risks, such as using government databases for ID […] The post The Benefits and Risks of Using Government Databases for ID Verification in Fraud Prevention appeared first on Security B

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

WIRED Threat Level
MARCH 19, 2023
Don't drink and tweet.

Security Boulevard
MARCH 19, 2023
Hong Sae is the CIO for the city of Roseville, Calif., and he has a tremendous track record of success in both Texas and California local government. The post Roseville, Calif., CIO Brings Global Background to Local Gov appeared first on Security Boulevard.

Penetration Testing
MARCH 19, 2023
Caido Caido aims to help security professionals and enthusiasts audit web applications with efficiency and ease. Feature Sitemap The Sitemap feature allows you to visualize the structure of any website that is proxied through... The post Caido v0.30 releases: audit web applications with efficiency and ease appeared first on Penetration Testing.
Security Boulevard
MARCH 19, 2023
2 min read Cyolo 4.0 has officially arrived! Discover all the details of this latest release, including (spoiler alert!) a simplified user login workflow and portal redesign. The post What’s New in Cyolo 4.0 appeared first on Cyolo. The post What’s New in Cyolo 4.0 appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
MARCH 19, 2023
Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Security ’22 Conference content on the organization’s’ YouTube channel. Permalink The post USENIX Security ’22 – Mohsen Minaei, Mainack Mondal, Aniket Kate – ‘Empirical Understanding Of Deletion Privacy: Experiences, Expectations, And Measures’ appeared first on Security Boulevard.
Let's personalize your content