Chinese Hacking of US Critical Infrastructure
Schneier on Security
MAY 31, 2023
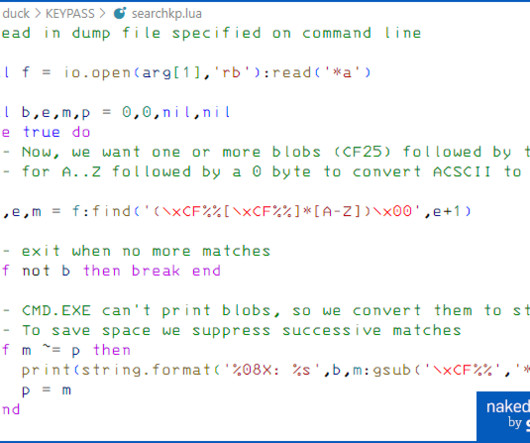
Everyone is writing about an interagency and international report on Chinese hacking of US critical infrastructure. Lots of interesting details about how the group, called Volt Typhoon , accesses target networks and evades detection.











































Let's personalize your content