Microsoft sent you a USB stick – what would you do?
Javvad Malik
JULY 25, 2022
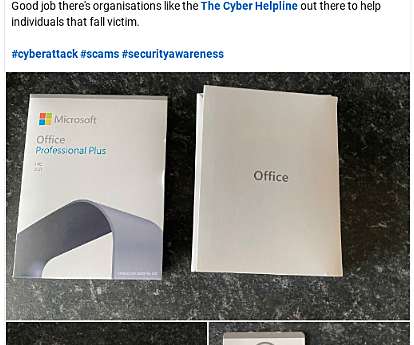
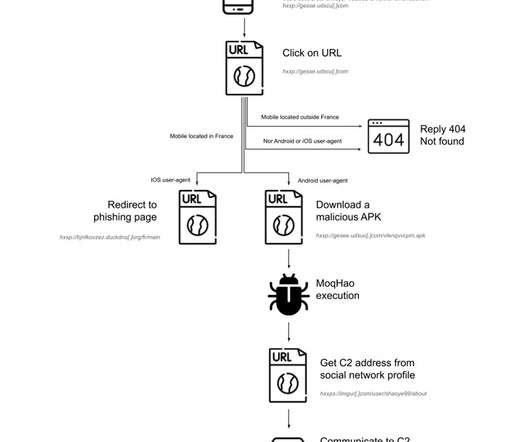
I saw this post on linkedin and was part disgusted, but also slightly admired the professionalism and thought that went into this scam. An unsuspecting victim was sent a USB drive that for all intents and purposes looked like it came from Microsoft. The packaging and logo all looks legit. This is where people’s biases will come into play. If they plug it in and there’s a popup asking “Are you sure” then unless they’re a bit savvy or paranoid, most people will click


































Let's personalize your content