Russian APT Gamaredon uses USB worm LitterDrifter against Ukraine
Security Affairs
NOVEMBER 18, 2023
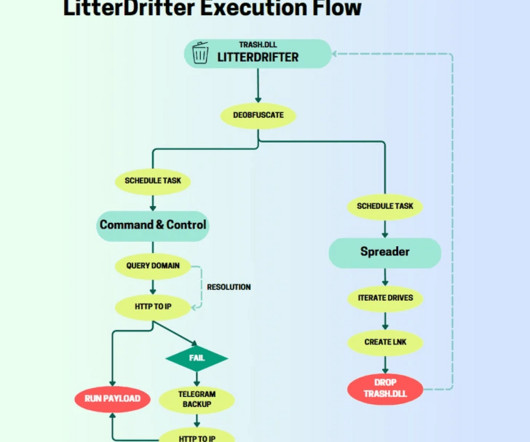
Russia-linked cyberespionage group Gamaredon has been spotted propagating a worm called LitterDrifter via USB. Check Point researchers observed Russia-linked Gamaredon spreading the worm called LitterDrifter via USB in attacks against Ukraine. Gamaredon (aka Shuckworm, Actinium, Armageddon, Primitive Bear, UAC-0010, and Trident Ursa) has been active since 2014 and its activity focuses on Ukraine, the group was observed using the multistage backdoor Pteranodon / Pterodo.


















Let's personalize your content