New Business Email Compromise Schemes Add Vendor Deception
Lohrman on Security
JULY 24, 2022
Like other forms of cyber crime, business email compromise is growing and evolving. Here’s what you need to know.

Lohrman on Security
JULY 24, 2022
Like other forms of cyber crime, business email compromise is growing and evolving. Here’s what you need to know.
Security Affairs
JULY 24, 2022
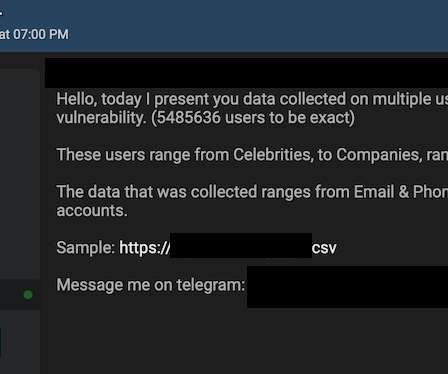
Threat actor leaked data of 5.4 million Twitter users that were obtained by exploiting a now patched flaw in the popular platform. A threat actor has leaked data of 5.4 million Twitter accounts that were obtained by exploiting a now-fixed vulnerability in the popular social media platform. The threat actor is now offering for sale the stolen data on a the popular hacking forum Breached Forums.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
JULY 24, 2022
Microsoft has reminded customers once again that Windows Server, version 20H2, will be reaching its End of Service (EOS) in less than a month, on August 9. [.].

Tech Republic Security
JULY 24, 2022
According to Gartner, the rapid evolution and sophistication of cyberattacks and the migration of assets to the hybrid multi-cloud create a perfect storm. IT leaders must integrate security tools into a cooperative, consolidated ecosystem using a composable and scalable cybersecurity mesh architecture (CSMA) approach. By 2024, organizations adopting a CSMA to integrate security tools to.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
Security Affairs
JULY 24, 2022
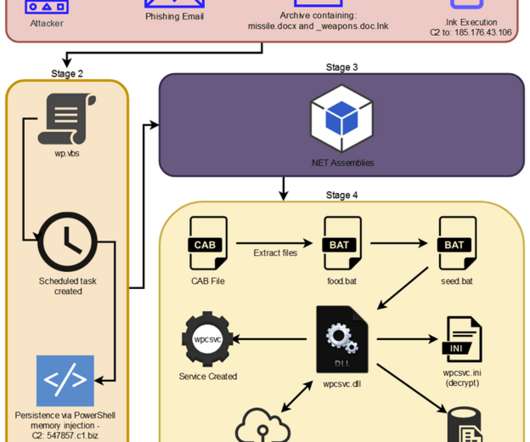
North Korea-linked APT37 group targets high-value organizations in the Czech Republic, Poland, and other countries. Researchers from the Securonix Threat Research (STR) team have uncovered a new attack campaign, tracked as STIFF#BIZON, targeting high-value organizations in multiple countries, including Czech Republic, and Poland. The researchers attribute this campaign to the North Korea-linked APT37 group, aka Ricochet Chollima.

Tech Republic Security
JULY 24, 2022
According to Gartner’s Case-Based Research, the three most pervasive challenges that AI addresses are lack of detection capability, inadequate security posture, and poor operational efficiency. In many ways, cybersecurity is becoming a big data problem, given the volume and sophistication of cybercampaigns. Fortunately, the application of artificial intelligence (AI) for cyberattack detection is a rapidly.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JULY 24, 2022
Over three-quarters of employees want the option to work from home at least part-time. The ability to support a remote work program can help an organization retain employees and is a crucial component of a business continuity plan. While not every remote worker needs a full corporate environment to do their jobs, some do. For. The post FortiAP Access Points Provide Secure, Painless Connectivity for Remote Workers appeared first on TechRepublic.

Security Boulevard
JULY 24, 2022
Our sincere thanks to Security BSides San Francisco for publishing their outstanding conference videos on the organization's YouTube channel. Permalink. The post BSidesSF 2022 – Kyle Tobener, MakeItHackin, shenetworks, Kylie Robison ‘Hacker TikTok: Community, Creativity, And Controversy’ appeared first on Security Boulevard.

Tech Republic Security
JULY 24, 2022
The rapid growth of personal and Internet-of-Things (IoT) devices connecting to enterprise networks has increased the need to have fine-grained control over what is allowed into the network and with what permissions. Network access control (NAC) solutions can ensure only devices that should attach to the network do, and can restrict what they have access.

WIRED Threat Level
JULY 24, 2022
The next time someone wants to borrow your device to make a call or take a picture, take these steps to protect your privacy.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
JULY 24, 2022
Today’s networks are expected to do more than deliver connectivity and bandwidth. To optimize performance and enable additional functionality, a network needs to be intelligent. The more intelligent the network, the better it will perform, and the more tasks it can offload from IT teams. A network that has built-in intelligence cuts down on the. The post How an Intelligent Network Can Unburden IT Teams – Checklist appeared first on TechRepublic.

Security Boulevard
JULY 24, 2022
When most people speak of any city government, they often mention words like “Bureaucratic”,“Behind the times”, and “Slow.” This is especially true when considering cybersecurity initiatives. However, a small town in Texas is changing that view. Seguin, Texas, which was once the smallest Texas city to have a full-time cybersecurity employee, was the only government […]… Read More.

Tech Republic Security
JULY 24, 2022
The wired and wireless local area network (LAN) forms the backbone of IT. It enables next-generation applications and can boost user productivity. As such, the LAN not only greatly impacts user experience, but is also the beginning or end of many security events. Today’s IT administrators need to build their next-generation networks with a focus. The post Not-So-Hidden Costs Are Lurking in the LAN: Insist on Operational and Licensing Simplicity appeared first on TechRepublic.

Acunetix
JULY 24, 2022
To fully secure your web applications, you need several software solutions, specialist internal resources, and external contractors. However, this means significant costs, and not everyone can afford it all at once. How should small businesses start their web application security journey? Let’s have a look. Read more. The post 3 reasons why DAST is the best way to begin the web application security journey appeared first on Acunetix.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
JULY 24, 2022
To stay competitive, a high-performing network that meets the needs of digital acceleration initiatives is critical. Sometimes it’s difficult to know what to focus on, as there are a lot of different factors that can impact performance, from the architecture chosen, to the age of the equipment, to the client devices. Another key contributor that. The post Why Security Is a Top Influencer of Network Performance appeared first on TechRepublic.

Bleeping Computer
JULY 24, 2022
A new version of the Amadey Bot malware is distributed through the SmokeLoader malware, using software cracks and keygen sites as lures. [.].

Tech Republic Security
JULY 24, 2022
Not to mention the negative financial impacts and reputational damage that ransomware can cause. The overall frequency of ransomware detections might be leveling off, but the sophistication, aggressiveness, and impact of this threat continues relentlessly. Threat actors continue to pound away at organizations with a variety of new and previously seen ransomware strains, often leaving.

Notice Bored
JULY 24, 2022
depending on others and being there for them when they need us most. the rod bending alarmingly. while landing a whopper. an oak tree growing roots against the prevailing wind. taking the punches, reeling but not out for the count. demonstrating, time after time, personal integrity. willingness to seize opportunities, taking chances. coping with social distancing, masks and all that. accumulating reserves for the bad times ahead. the bloody-minded determination to press on. disregardin g trivia,

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Tech Republic Security
JULY 24, 2022
Ransomware has become a popular weapon in the hands of malicious actors who try to harm governments, businesses, and individuals daily. Ransomware is the final stage of a more complex attack. The security breach could have already happened a long time ago. Considering the range and volume of cyberattacks that organizations face daily, a disjointed. The post IDC Building Ransomware Resilience appeared first on TechRepublic.

Security Boulevard
JULY 24, 2022
via the textual amusements of Thomas Gx , along with the Illustration talents of Etienne Issartia and superb translation skillset of Mark Nightingale - the creators of CommitStrip ! Permalink. The post CommitStrip ‘Don’t Even Need To Pretend Any More’ appeared first on Security Boulevard.

Tech Republic Security
JULY 24, 2022
Endpoint security solutions range from the original antivirus solutions of yesteryear to extended detection and response (XDR) platforms that tie multiple security solutions together for a better ecosystem. As the needs arise for endpoint security solutions, vendors will attempt to make their solutions match buyer expectations and analyst terms through their messaging but not their.

Security Boulevard
JULY 24, 2022
Like other forms of cyber crime, business email compromise is growing and evolving. Here’s what you need to know. The post New Business Email Compromise Schemes Add Vendor Deception appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
JULY 24, 2022
Many of today’s cyberattacks are broken into multiple stages of activity, each of which on its own is often difficult to discern as malicious rather than benign. Discernment is even more difficult given the volume of legitimate activity within which it naturally occurs given the diversity of work styles, devices, networks, applications, and cloud-delivery locations.

Security Boulevard
JULY 24, 2022
Our sincere thanks to Security BSides San Francisco for publishing their outstanding conference videos on the organization's YouTube channel. Permalink. The post BSidesSF 2022 – Omid Mirzaei’s ‘Practical Threat Hunting With Machine Learning’ appeared first on Security Boulevard.

Tech Republic Security
JULY 24, 2022
According to the Fortinet February 2022 Global Threat Landscape Report, industries worldwide experienced a dramatic 15x growth in ransomware volume over the past 18 months, with sustained volume throughout 2021. Furthermore, attacks are harder to stop because of the evolution of increasing capabilities thanks to a very active economy of threat actors with fresh code.

Notice Bored
JULY 24, 2022
While arguably better than nothing at all, an unstructured approach to the management of information security results in organisaitons adopting a jumble, a mixed bag of controls with no clear focus or priorities and – often – glaring holes in the arrangements. The lack of structure indicates the absense of genuine management understanding, commitment and support that is necessary to give information risk and security due attention - and sufficient resourcing - throughout the business.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
JULY 24, 2022
Today’s organizations have a broad digital attack surface spanning a diverse set of devices, user locations, networks, and clouds, providing many avenues of entry and exfiltration for cybercriminals. Increasingly, these cybercriminals are doing more than stealing data, often encrypting whole systems and interrupting business operations with ransomware, a threat that’s increased 15x over the past.

Tech Republic Security
JULY 24, 2022
Endpoint security solutions range from signature-based endpoint protection platform (EPP) or antivirus (AV) solutions to extended detection and response (XDR) platforms that tie multiple security solutions together. Organizations that are evaluating endpoint detection and response (EDR) solutions need to ensure that the products they are considering will meet their needs in the following areas.
Let's personalize your content