ChatGPT: Hopes, Dreams, Cheating and Cybersecurity
Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?

Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?
Security Boulevard
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains? The post ChatGPT: Hopes, Dreams, Cheating and Cybersecurity appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
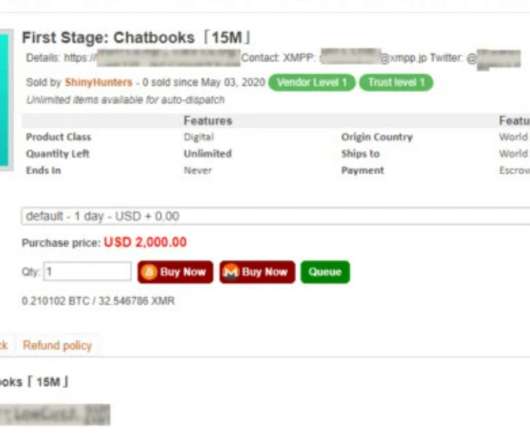
Security Affairs
JANUARY 29, 2023
An alleged member of the ShinyHunters cybercrime gang has been extradited from Morocco to the United States. Sebastien Raoult, a French national who is suspected of being a member of ShinyHunters cybercrime gang known as “Seyzo Kaizen,” has been extradited from Morocco to the United States. The 22-year-old man was arrested in Morocco at Rabat international airport in Morocco on May 31, 2022, while trying to take a flight to Brussels.

Malwarebytes
JANUARY 29, 2023
As war in Ukraine rages, new destructive malware continues to be discovered. In a recent tweet , the Ukrainian Computer Emergency Response Team (CERT-UA) named five wipers used against Ukrinform, Ukraine’s national news agency. It suspects a link to the Sandworm group. UPDATE: UAC-0082 (suspected #Sandworm ) to target Ukrinform using 5 variants of destructive software: CaddyWiper, ZeroWipe, SDelete, AwfulShred, BidSwipe.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
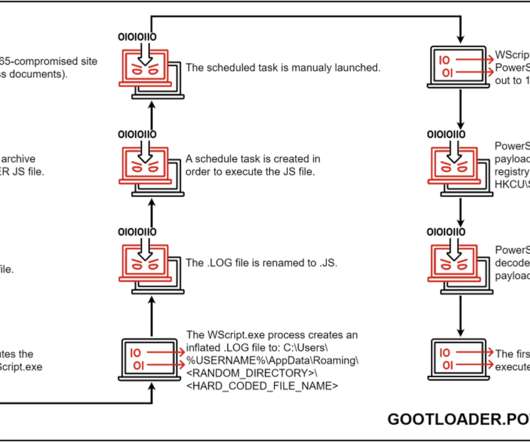
Security Affairs
JANUARY 29, 2023
The threat actors behind the GOOTLOADER malware continues to improve their code by adding new components and implementing new obfuscation techniques. Mandiant researchers reported that the UNC2565 group behind the GOOTLOADER malware (aka Gootkit ) continues to improve their code by adding new components and implementing new obfuscation techniques. Gootkit runs on an access-a-as-a-service model, it is used by different groups to drop additional malicious payloads on the compromised systems.

Bleeping Computer
JANUARY 29, 2023
A new category of activity tracking applications has been having massive success recently on Google Play, Android's official app store, having been downloaded on over 20 million devices. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
JANUARY 29, 2023
Last week on Malwarebytes Labs: T-Mobile reports data theft of 37 million customers in the US Ransomware revenue significantly down over 2022 Microsoft to end direct sale of Windows 10 licenses at the end of January TikTok CEO told to "step up efforts to comply" with digital laws 4 ways to protect your privacy while scrolling Key takeaways from Malwarebytes 2023 State of Mobile Cybersecurity Riot Games compromised, new releases and patches halted What privacy can get you VASTFLUX ad fraud massiv

Security Affairs
JANUARY 29, 2023
Horizon3’s Attack Team made the headlines again announcing the releasse of a PoC exploit code for remote code execution in VMware vRealize Log. Researchers from the Horizon3’s Attack Team announced the release of PoC exploit code for remote code execution in VMware vRealize Log. Exploitation of multiple vulnerabilities affecting #VMware vRealize Log Insight leads to unauth RCE CVE-2022-31704, CVE-2022-31706, CVE-2022-31711 IOC Blog tomorrow POC / Deep-Dive Blog next week See VMware S

Security Boulevard
JANUARY 29, 2023
What is Video KYC? Video KYC (Know Your Customer) is a process for customer Identity verification using remote video technology. It is a secure and efficient way for financial institutions, online businesses, and other organizations to verify the identity of their customers without requiring them to physically visit a branch or office. Why use Video […] The post Video Verification API: The Technology Behind Video KYC appeared first on Security Boulevard.
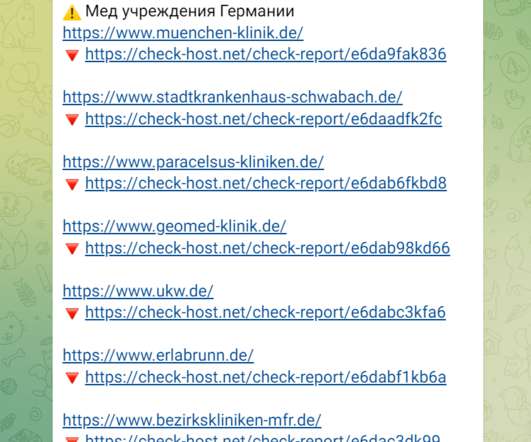
Security Affairs
JANUARY 29, 2023
Pro-Russia group Killnet launched last week DDoS attacks against the websites of German airports, administration bodies, and banks. The Pro-Russia group Killnet is behind the DDoS attacks that last week hit the websites of German airports, administration bodies, and banks. The attacks are the hacktivists’ response to the German government’s decision to send Leopard 2 tanks to Ukraine.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
JANUARY 29, 2023
Complete Title : 'USENIX Security '22 - Le Yu, Yangyang Liu, Pengfei Jing, Xiapu Luo, Lei Xue, Kaifa Zhao, Yajin Zhou, Ting Wang, Guofei Gu, Sen Nie, Shi Wu - ‘Towards Automatically Reverse Engineering Vehicle Diagnostic Protocols’' Permalink The post USENIX Security ’22 – ‘Towards Automatically Reverse Engineering Vehicle Diagnostic Protocols’ appeared first on Security Boulevard.

The Last Watchdog
JANUARY 29, 2023
The cybersecurity profession can be very rewarding, but at the same time quite taxing. Related: Equipping SOCs for the long haul In fact, stress factors have risen to where some 45 percent of the security professionals polled in Deep Instinct’s third annual Voice of SecOps report said they’ve considered leaving the industry altogether. Ransomware is at an all-time high; attackers are as elusive as ever.
Let's personalize your content