BlackCat ransomware pushes Cobalt Strike via WinSCP search ads
Bleeping Computer
JULY 1, 2023
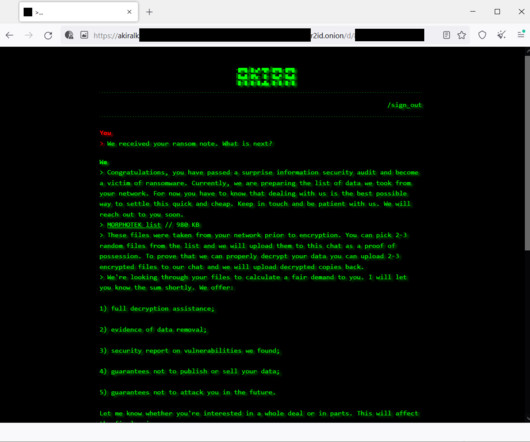
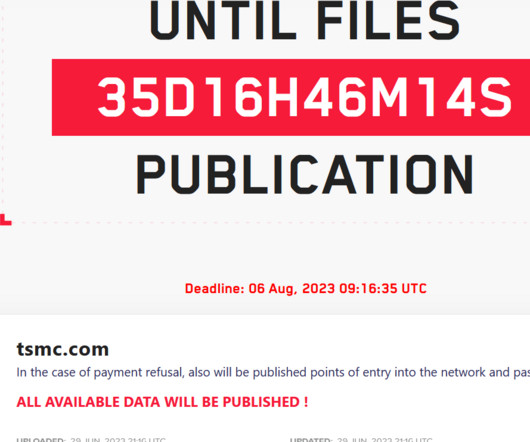
The BlackCat ransomware group (aka ALPHV) is running malvertizing campaigns to lure people into fake pages that mimic the official website of the WinSCP file-transfer application for Windows but instead push malware-ridden installers. [.














Let's personalize your content