Arrest, Seizures Tied to Netwalker Ransomware
Krebs on Security
JANUARY 27, 2021
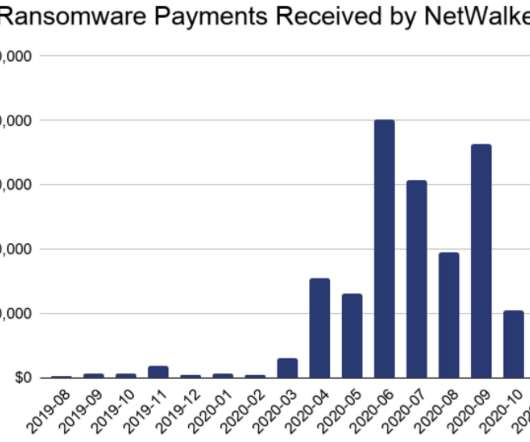
U.S. and Bulgarian authorities this week seized the darkweb site used by the NetWalker ransomware cybercrime group to publish data stolen from its victims. In connection with the seizure, a Canadian national suspected of extorting more than $27 million through the spreading of NetWalker was charged in a Florida court. The victim shaming site maintained by the NetWalker ransomware group, after being seized by authorities this week.


































Let's personalize your content