Innovation, Agility and Securing the Mobile World in 2021
Lohrman on Security
FEBRUARY 21, 2021

Bleeping Computer
FEBRUARY 21, 2021
Threat actors are using Google Alerts to promote a fake Adobe Flash Player updater that installs other unwanted programs on unsuspecting users' computers. [.].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Identity IQ
FEBRUARY 21, 2021
Identity theft insurance is a type of insurance policy that can help victims recover from losses caused by identity theft. It may be offered as a standalone policy, or as a benefit with other types of insurance or identity protection plans. Not all identity theft insurance policies offer the same level of coverage. If you’re considering identity theft insurance, it’s important to understand the types of losses that identity theft causes and what losses identity theft insurance policies may cover
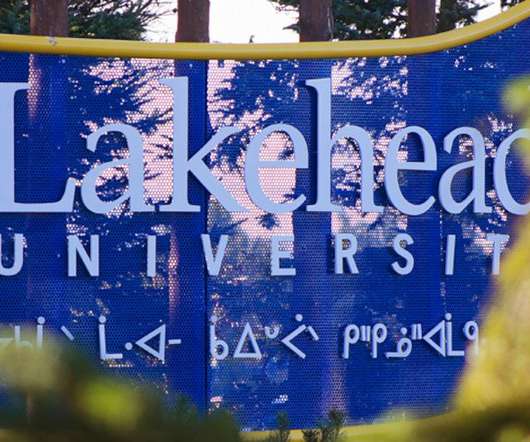
Bleeping Computer
FEBRUARY 21, 2021
Canadian undergraduate research university Lakehead has been dealing with a cyberattack that forced the institution earlier this week to cut off access to its servers. [.].

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
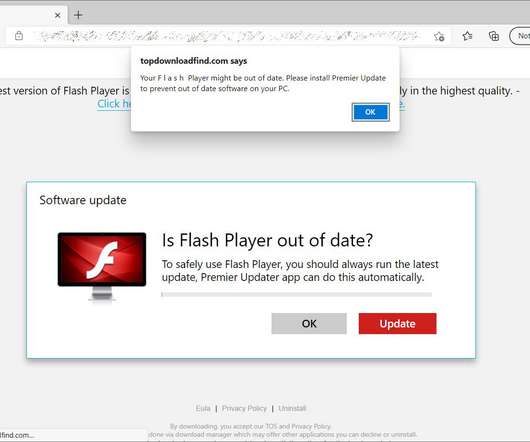
Security Affairs
FEBRUARY 21, 2021
Experts warn of threat actors using Google Alerts to promote a fake Adobe Flash Player updater that delivers unwanted programs. Experts from BleepingComputer are warning of threat actors that are using Google Alerts to promote a fake Adobe Flash Player updater that delivers unwanted programs. Bad actors publish posts with titles containing popular keywords to allow Google Search to index the content.

Bleeping Computer
FEBRUARY 21, 2021
Microsoft is adding support for sending emails via alias email addresses (also known as aliases or proxy addresses) from the Outlook for Windows email client. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
FEBRUARY 21, 2021
With the upcoming Windows 10 21H1 feature update being a minor release with few improvements, Microsoft will likely include all of the new features they have introduced in Insider builds in Windows 10 21H2. These new features are outlined below. [.].

Security Boulevard
FEBRUARY 21, 2021
Our thanks to BSidesSF and Conference Speakers for publishing their outstanding presentations; which originally appeared at the group's BSidesSF 2020 Conference , and on the Organization's YouTube Channel. Additionally, the BSidesSF 2021 Conference will take place on March 6 - 9, 2021 - with no cost to participate. Enjoy! Permalink. The post BSidesSF 2020 – Atul Gaikwad’s & Moses Schwartz’ ‘Mistakes Made Integrating Security Scanning Into CI/CD’ appeared first o

Bleeping Computer
FEBRUARY 21, 2021
Google Chrome for iOS is getting a new privacy feature that lets you lock your opened Incognito tabs behind your iPhone's Face ID or Touch ID biometric authentication features. [.].

Security Affairs
FEBRUARY 21, 2021
A white hat hacker has earned a $5,000 reward from Apple for reporting a stored cross-site scripting (XSS) vulnerability on iCloud.com. The bug bounty hunter Vishal Bharad has earned a $5,000 reward from Apple for reporting a stored cross-site scripting (XSS) vulnerability on iCloud.com. Bharad was searching for cross-site request forgery (CSRF), insecure direct object reference (IDOR), and other vulnerabilities in the Apple icloud.com website, when he found a stored XSS vulnerability.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
FEBRUARY 21, 2021
The fastest way to lose credibility with your customers is to breach their sense of security. Your clients trust you to protect them and their information whether you are interacting with them online or in person. You must consider their safety as one of the top priorities of every transaction you complete. Often your customers [.]. The post 6 Security Methods to Protect You and Your Customers appeared first on TechSpective.
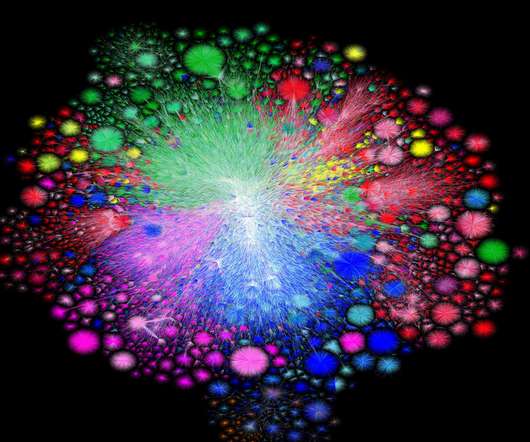
WIRED Threat Level
FEBRUARY 21, 2021
In 2003, Barrett Lyon created a map of the internet. In 2021, he did it again—and showed just how quickly it's expanded.

Security Affairs
FEBRUARY 21, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. PayPal addresses reflected XSS bug in user wallet currency converter The kingpin behind Jokers Stash retires with a billionaire exit France agency ANSSI links Russias Sandworm APT to attacks on hosting providers French and Ukrainian police arrested Egregor ransomware a

CyberSecurity Insiders
FEBRUARY 21, 2021
This post was originally published by Will Houcheime. The vast majority of healthcare organizations utilize and store highly sensitive data, such as protected health information (PHI) and personal data such Social Security numbers, personal financial data , and more. For our annual Healthcare Breach Report, we analyzed data from the US Department of Health and Human Services’ “Wall of Shame” to get a closer look at the state of security for healthcare organizations over the last few years.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
FEBRUARY 21, 2021
via the respected information security capabilities of Robert M. Lee & the superlative illustration talents of Jeff Haas at Little Bobby Comics. Permalink. The post Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 317’ appeared first on Security Boulevard.

CyberSecurity Insiders
FEBRUARY 21, 2021
This post was originally published by (ISC)² Management. For a limited time – February 22-28, 2021 – (ISC)² is pilot testing the option to take the CISSP online exam from home. Last year, as the COVID-19 pandemic emerged, we accelerated our exploration of enabling candidates to take the CISSP exam online. While all (ISC)² exams are, and will remain, available to be taken in person at test centers with health and safety measures in place , we are happy to be able to offer an alternative in th

Security Boulevard
FEBRUARY 21, 2021
As the use of mobile devices has become ubiquitous around the world, the cybersecurity imperative for a wide range of devices and mobile apps has become a central issue for most organizations. So how do leading global companies address mobile security for clients and staff? Where have we been over the past few years and. The post Innovation, Agility and Securing the Mobile World in 2021 appeared first on Security Boulevard.

Bleeping Computer
FEBRUARY 21, 2021
Google Chrome for iOS is getting a new privacy feature that lets you lock your opened Incognito tabs behind your iPhone's Face ID or Touch ID biometric authentication features. [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
FEBRUARY 21, 2021
Our thanks to BSidesSF and Conference Speakers for publishing their outstanding presentations; which originally appeared at the group's BSidesSF 2020 Conference , and on the Organization's YouTube Channel. Additionally, the BSidesSF 2021 Conference will take place on March 6 - 9, 2021 - with no cost to participate. Enjoy! Permalink. The post BSidesSF 2020 – Yu-Jye Tung’s ‘An Effective Approach To Software Obfuscation’ appeared first on Security Boulevard.

Spinone
FEBRUARY 21, 2021
This article is for IT administrators, or SMB owners looking for ways to protect their business-critical SaaS data. It explains how to backup Office 365. What makes the best backup tool for your O365 data? There are many factors to this, but the main ones are: Automation and frequency Recovery speed and accuracy Security and […] The post How to Backup Office 365: Best Cloud Tool for IT Admin & CEO in 2021 first appeared on SpinOne.
Let's personalize your content