Mac malware-for-hire steals passwords and cryptocoins, sends “crime logs” via Telegram
Naked Security
APRIL 29, 2023
These malware peddlers are specifically going after Mac users. The hint's in the name: "Atomic macOS Stealer", or AMOS for short.

Naked Security
APRIL 29, 2023
These malware peddlers are specifically going after Mac users. The hint's in the name: "Atomic macOS Stealer", or AMOS for short.

Bleeping Computer
APRIL 29, 2023
Veeam backup servers are being targeted by at least one group of threat actors known to work with multiple high-profile ransomware gangs. [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
APRIL 29, 2023
Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Enigma ’23 Conference content on the organization’s’ YouTube channel. Permalink The post USENIX Enigma 2023 – Kenn White, MongoDB – ‘The Edge Of Developed Practice In Searching Encrypted Data’ appeared first on Security Boulevard.

Security Affairs
APRIL 29, 2023
A new variant of the information-stealing malware ViperSoftX implements sophisticated techniques to avoid detection. Trend Micro researchers observed a new ViperSoftX malware campaign that unlike previous attacks relies on DLL sideloading for its arrival and execution technique. #ViperSoftX is back, doesn't look like much has changed. c2 arrowlchat[.]com Still fetching powershell txt records from privatproxy-schnellvpn[.]xyz pic.twitter.com/VLhISark8Y — Goldwave (@OGoldwave) March 13,

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

WIRED Threat Level
APRIL 29, 2023
Maybe you don't want your phone number, email, home address, and other details out there for all the web to see. Here's how to make them vanish.

Security Affairs
APRIL 29, 2023
U.S. CISA released an Industrial Control Systems (ICS) medical advisory warning of a critical flaw affecting Illumina medical devices. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released an Industrial Control Systems (ICS) medical advisory warning of vulnerabilities that could allow an attacker to take any action at the operating system level.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
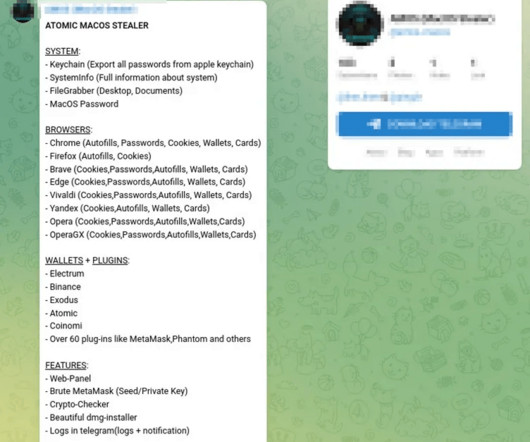
Security Affairs
APRIL 29, 2023
Atomic macOS Stealer is a new information stealer targeting macOS that is advertised on Telegram for $1,000 per month. Cyble Research and Intelligence Labs (CRIL) recently discovered a Telegram channel advertising a new information-stealing malware, named Atomic macOS Stealer (AMOS). The malware targets macOS, it was designed to steal sensitive information from the infected systems.

WIRED Threat Level
APRIL 29, 2023
Plus: Cyber Command’s disruption of Iranian election hacking, an exposé on child sex trafficking on Meta’s platforms, and more.
Hacker's King
APRIL 29, 2023
This is one of the most frequently asked questions to me, "How to find someone on the Internet.” Probably wherever you go to parties or marriages, you see a girl and want to know her Instagram ID, and then you start asking your friends about her. So in this article, I’ll help you find someone on social media or the Internet by using their face picture.
Let's personalize your content