Pharmacies Giving Patient Records to Police without Warrants
Schneier on Security
JANUARY 11, 2024
Add pharmacies to the list of industries that are giving private data to the police without a warrant.

Schneier on Security
JANUARY 11, 2024
Add pharmacies to the list of industries that are giving private data to the police without a warrant.

Tech Republic Security
JANUARY 11, 2024
Looking for the best anonymous (no-log) VPN? Check out our comprehensive list to find the top VPN services that prioritize anonymity and security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
JANUARY 11, 2024
Hackers have found a way to gain unauthorized access to Google accounts, bypassing any multi-factor authentication (MFA) the user may have set up. To do this they steal authentication cookies and then extend their lifespan. It doesn’t even help if the owner of the account changes their password. Since the discovery of the exploit, numerous white and black hat security researchers have looked into and discussed the issue.

Bleeping Computer
JANUARY 11, 2024
Two vulnerabilities impacting the POST SMTP Mailer WordPress plugin, an email delivery tool used by 300,000 websites, could help attackers take complete control of a site authentication. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Trend Micro
JANUARY 11, 2024
This blog delves into the Phemedrone Stealer campaign's exploitation of CVE-2023-36025, the Windows Defender SmartScreen Bypass vulnerability, for its defense evasion and investigates the malware's payload.

Bleeping Computer
JANUARY 11, 2024
Microsoft has released a PowerShell script to automate updating the Windows Recovery Environment (WinRE) partition in order to fix CVE-2024-20666, a vulnerability that allowed for BitLocker encryption bypass. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
JANUARY 11, 2024
The Finish National Cybersecurity Center (NCSC-FI) is informing of increased Akira ransomware activity in December, targeting companies in the country and wiping backups. [.
Security Boulevard
JANUARY 11, 2024
Federal regulators are banning OutLogic from selling or sharing sensitive location data to third parties, marking the latest effort by government officials to address the thorny issue of data brokers and what they do with the massive amounts of personal information they collect. In this case, the Federal Trade Commission (FTC), in its first settlement.

eSecurity Planet
JANUARY 11, 2024
When remote workers connect bring-your-own-device (BYOD) laptops, desktops, tablets, and phones to corporate assets, risk dramatically increases. These devices exist outside of direct corporate management and provide a ransomware gang with unchecked platforms for encrypting data. Ransomware remains just one of many different threats and as security teams eliminate key vectors of attack, adversaries will shift tactics.

Bleeping Computer
JANUARY 11, 2024
The open-source Bitwarden password manager has announced that all users can now log in to their web vaults using a passkey instead of the standard username and password pairs. [.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
JANUARY 11, 2024
This article is part of a series where we look at a recent NSA/CISA Joint Cybersecurity Advisory on the top cybersecurity issues identified during red/blue team exercises operated by these organizations. In this article, you will find a more in-depth look at the specific issue, with real-world scenarios where it is applicable, as well as […] The post Insufficient Internal Network Monitoring in Cybersecurity appeared first on TuxCare.

Security Affairs
JANUARY 11, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Ivanti Connect Secure and Microsoft SharePoint bugs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added an Ivanti Connect Secure and Policy Secure flaws, tracked as CVE-2024-21887 and CVE-2023-46805 , and Microsoft SharePoint Server flaw CVE-2023-29357 to its Known Exploited Vulnerabilities (KEV) catalog.

Security Boulevard
JANUARY 11, 2024
Build your cybersecurity strategy on a solid foundation of asset visibility and segmentation On November 20, 2023, the Cybersecurity Infrastructure and Security Agency (CISA) issued guidance for healthcare delivery organizations (HDOs) struggling to secure their data and systems against a growing and pernicious onslaught of attacks from threat actors across the globe.

Bleeping Computer
JANUARY 11, 2024
Framework Computer disclosed a data breach exposing the personal information of an undisclosed number of customers after Keating Consulting Group, its accounting service provider, fell victim to a phishing attack. [.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Affairs
JANUARY 11, 2024
Ivanti revealed that two threat actors are exploiting two zero-day vulnerabilities in its Connect Secure (ICS) and Policy Secure. Software firm Ivanti reported that threat actors are exploiting two zero-day vulnerabilities (CVE-2023-46805, CVE-2024-21887) in Connect Secure (ICS) and Policy Secure to remotely execute arbitrary commands on targeted gateways.
Bleeping Computer
JANUARY 11, 2024
A major T-Mobile outage is preventing customers from logging into their accounts and using the company's mobile app.

Security Boulevard
JANUARY 11, 2024
Software development continues to swiftly advance and also to entail more complex dependencies, with continuous integration/continuous development (CI/CD) bringing faster code releases. Meanwhile, application security (AppSec) is struggling to keep up with its practices and tooling. The post The evolution of AppSec: 4 key changes required for a new era appeared first on Security Boulevard.

Penetration Testing
JANUARY 11, 2024
The Linux Kernel has been hit by a significant security vulnerability, CVE-2023-6040, with a CVSS score of 7.8, impacting its netfilter component. Discovered by Lin Ma from Ant Security Light-Year Lab, this flaw arises... The post CVE-2023-6040: A Critical Linux Kernel Netfilter Vulnerability appeared first on Penetration Testing.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Malwarebytes
JANUARY 11, 2024
Software vendor Ivanti has warned customers about two actively exploited vulnerabilities in all supported versions of Ivanti Connect Secure and Ivanti Policy Secure Gateways. Successful exploitation would give an attacker the ability to run arbitrary code on Ivanti’s Virtual Private Network (VPN) system. The warning is echoed by several international security agencies like CISA and the German BSI.
Security Boulevard
JANUARY 11, 2024
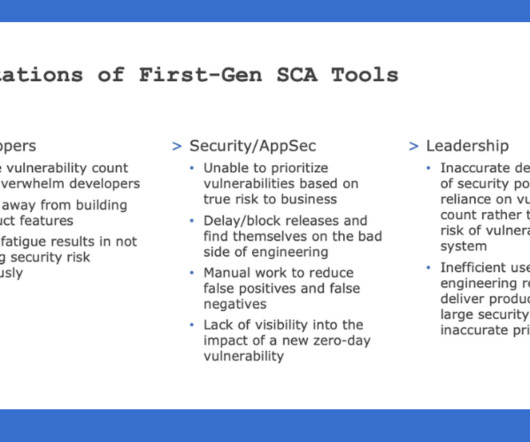
Read more » The post Prioritize Risk and Eliminate SCA Alert Fatigue with SCA 2.0 appeared first on Deepfactor. The post Prioritize Risk and Eliminate SCA Alert Fatigue with SCA 2.0 appeared first on Security Boulevard.

Penetration Testing
JANUARY 11, 2024
Multiple vulnerabilities were identified in Juniper Junos OS, posing a range of threats from denial of service to remote code execution. CVE-2024-21611: A memory leak and eventually an rpd crash Among these, a vulnerability has... The post CVE-2024-21591: Critical Pre-RCE Flaw Threatens Junos OS SRX and EX Series appeared first on Penetration Testing.

WIRED Threat Level
JANUARY 11, 2024
Crypto tracing firm Chainalysis found that sellers of child sexual abuse materials are successfully using “mixers” and “privacy coins” like Monero to launder their profits and evade law enforcement.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Penetration Testing
JANUARY 11, 2024
ShellSweep “ShellSweep” is a PowerShell/Python/Lua tool designed to detect potential webshell files in a specified directory. ShellSheep and its suite of tools calculate the entropy of file contents to estimate the likelihood of a... The post ShellSweep: detect potential webshell files in a specified directory appeared first on Penetration Testing.

SecureWorld News
JANUARY 11, 2024
Cybersecurity threats are a growing menace, wreaking havoc on businesses and individuals alike. In this digital battlefield, cyber insurance has emerged as a crucial shield, offering financial protection against data breaches, ransomware attacks, and other cyber incidents. However, just as the threats evolve, so too does the cost of protection, with the global cyber insurance market projected to balloon to a staggering $90. 6 billion by 2033, according to a recent report from Market.us Scoop.

Penetration Testing
JANUARY 11, 2024
In the ever-evolving landscape of cyber threats, GitLab, a renowned player in the DevOps field, has recently taken decisive steps to fortify its defenses against a series of critical vulnerabilities. CVE-2023-7028: Account Takeover via... The post CVE-2023-7028 & 5356: GitLab Addresses Account Takeover & Command Flaws appeared first on Penetration Testing.

Malwarebytes
JANUARY 11, 2024
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Identity IQ
JANUARY 11, 2024
New AI Scams to Look Out For in 2024 IdentityIQ Artificial intelligence (AI) has quickly reshaped many aspects of everyday life. As it continues to evolve and be normalized, criminals are finding creative new ways to wield AI as a weapon against our personal information and finances. The more aware you are of these tactics, the safer you can be from them.

The Hacker News
JANUARY 11, 2024
A new Python-based hacking tool called FBot has been uncovered targeting web servers, cloud services, content management systems (CMS), and SaaS platforms such as Amazon Web Services (AWS), Microsoft 365, PayPal, Sendgrid, and Twilio.

Penetration Testing
JANUARY 11, 2024
ModelScan: Protection Against Model Serialization Attacks Machine Learning (ML) models are shared publicly over the internet, within teams, and across teams. The rise of Foundation Models have resulted in public ML models being increasingly... The post modelscan: Protection against Model Serialization Attacks appeared first on Penetration Testing.

Bleeping Computer
JANUARY 11, 2024
A new Balada Injector campaign launched in mid-December has infected over 6,700 WordPress websites using a vulnerable version of the Popup Builder campaign. [.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content