xz Utils Backdoor
Schneier on Security
APRIL 2, 2024
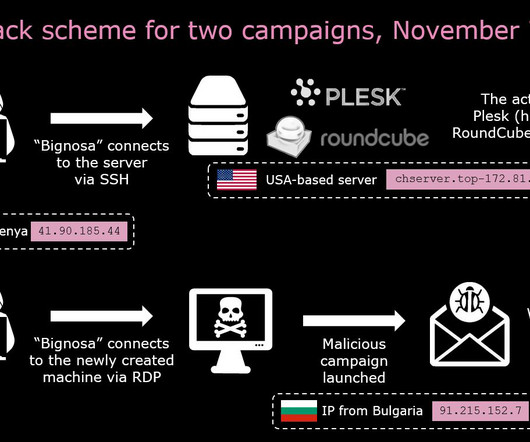
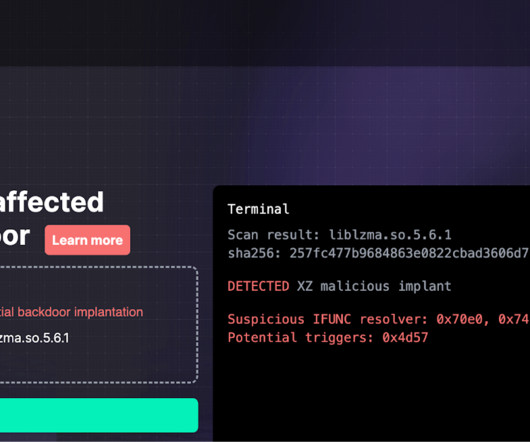
The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source compression utility, was pretty much accidentally discovered by a Microsoft engineer—weeks before it would have been incorporated into both Debian and Red Hat Linux. From ArsTehnica : Malicious code added to xz Utils versions 5.6.0 and 5.6.1 modified the way the software functions.



































Let's personalize your content