Atomic Stealer malware strikes macOS via fake browser updates
Bleeping Computer
NOVEMBER 25, 2023
The 'ClearFake' fake browser update campaign has expanded to macOS, targeting Apple computers with Atomic Stealer (AMOS) malware.

Bleeping Computer
NOVEMBER 25, 2023
The 'ClearFake' fake browser update campaign has expanded to macOS, targeting Apple computers with Atomic Stealer (AMOS) malware.
Security Affairs
NOVEMBER 25, 2023
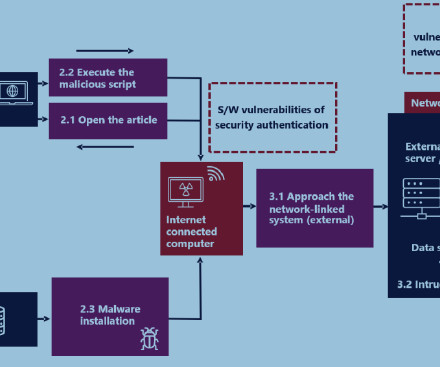
UK and South Korea agencies warn that North Korea-linked APT Lazarus is using a MagicLine4NX zero-day flaw in supply-chain attack The National Cyber Security Centre (NCSC) and Korea’s National Intelligence Service (NIS) released a joint warning that the North Korea-linked Lazarus hacking group is exploiting a zero-day vulnerability in the MagicLine4NX software to carry out supply-chain attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
NOVEMBER 25, 2023
General Electric is investigating claims that a threat actor breached the company's development environment in a cyberattack and leaked allegedly stolen data. [.

Penetration Testing
NOVEMBER 25, 2023
Security researcher Matei “Mal” Badanoiu disclosed the proof-of-concept (PoC) of a patched code execution vulnerability (CVE-2023-34212) that has been found to impact Apache NiFi. Assigned a CVSS score of 6.5, the flaw allows for... The post PoC Exploit Released for Apache NiFi Code Execution Vulnerability (CVE-2023-34212) appeared first on Penetration Testing.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

WIRED Threat Level
NOVEMBER 25, 2023
Plus: North Korean supply chain attacks, a Russian USB worm spreads internationally, and more.

Penetration Testing
NOVEMBER 25, 2023
In the murky world of cyber espionage, where nation-states and sophisticated hacking groups vie for secrets and intellectual property, the Dutch chipmaker NXP found itself at the center of a clandestine operation. For nearly... The post Chinese Hacker Group Chimera Invaded Dutch Chipmaker NXP for Nearly Three Years appeared first on Penetration Testing.
Security Affairs
NOVEMBER 25, 2023
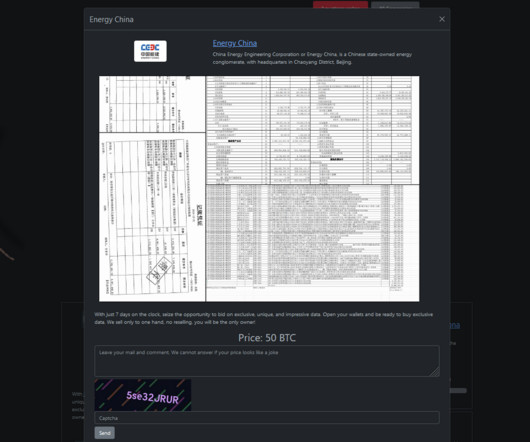
The Rhysida ransomware group claimed to have hacked the Chinese state-owned energy conglomerate China Energy Engineering Corporation. The Rhysida ransomware gang added the China Energy Engineering Corporation to the list of victims on its Tor leak site. Energy China [link] TL;DR That's huuuge! China Energy Engineering Group ranks 3rd in ENR Top 150 Global Engineering Design Firms and 13th in ENR Top 250 Global Contractors.
Let's personalize your content