Weekly Update 387
Troy Hunt
FEBRUARY 17, 2024
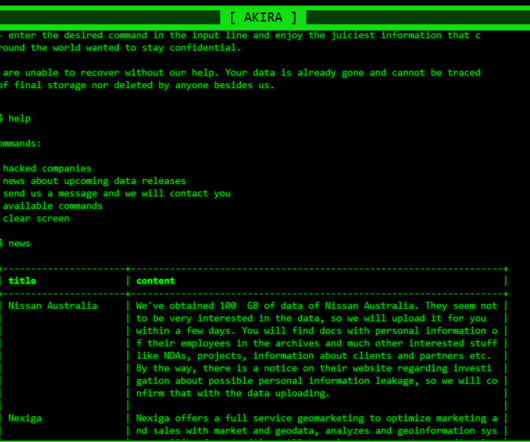
It's a short video this week after a few days in Sydney doing both NDC and the Azure user group. For the most part, I spoke about the same things as I did at NDC Security in Oslo last month. except that since then we've had the Spoutibe incident. It was fascinating to talk about this in front of a live audience and see everyone's reactions first hand, let's just say there were a lot of "oh wow!






















Let's personalize your content