REvil Ransom Arrest, $6M Seizure, and $10M Reward
Krebs on Security
NOVEMBER 8, 2021
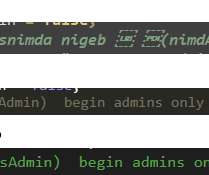
The U.S. Department of Justice today announced the arrest of Ukrainian man accused of deploying ransomware on behalf of the REvil ransomware gang, a Russian-speaking cybercriminal collective that has extorted hundreds of millions from victim organizations. The DOJ also said it had seized $6.1 million in cryptocurrency sent to another REvil affiliate, and that the U.S.











































Let's personalize your content