Generative AI Can Write Phishing Emails, But Humans Are Better At It, IBM X-Force Finds
Tech Republic Security
OCTOBER 24, 2023
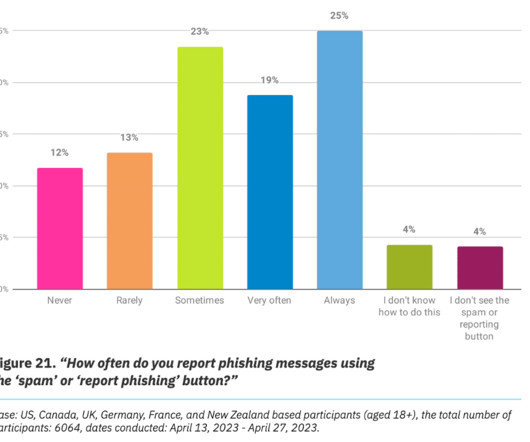
Hacker Stephanie "Snow" Carruthers and her team found phishing emails written by security researchers saw a 3% better click rate than phishing emails written by ChatGPT.





































Let's personalize your content