PayPal scam abuses Docusign API to spread phishy emails
Malwarebytes
MARCH 4, 2025
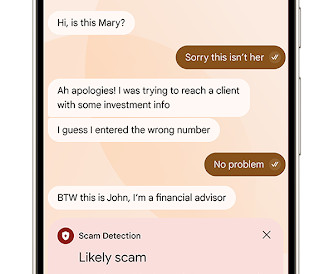
PayPal scammers are using an old Docusign trick to enhance the trustworthiness of their phishing emails. We’ve received several reports of this recently, so we dug into how the scam works. The Docusign Application Programming Interface (API) allows customers to send emails that come from genuine Docusign accounts, and they can use templates to impersonate reputable companies.







































Let's personalize your content