Securing Linux Policy
Tech Republic Security
SEPTEMBER 4, 2023
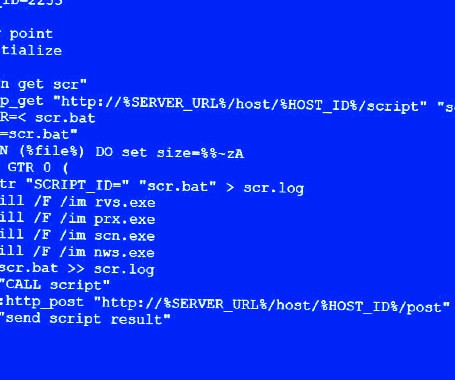
Linux is a powerful and customizable operating system that has been the backbone of many businesses for decades. This policy from TechRepublic Premium provides guidelines for securing Linux on company computers and computers used to conduct company business. It assumes administrative knowledge of Linux servers and/or workstation environments. From the policy: DEVELOP TEMPLATES BASED ON.







































Let's personalize your content