Faking an iPhone Reboot
Schneier on Security
JANUARY 12, 2022
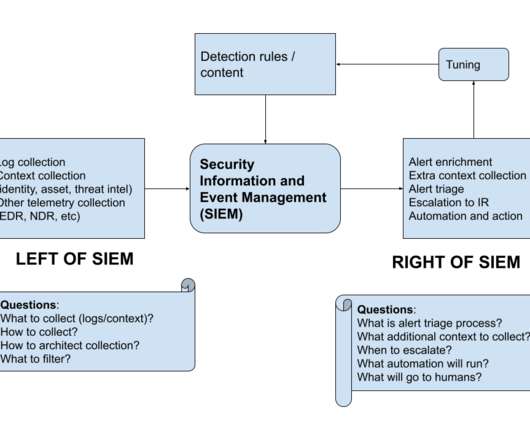
Researchers have figured how how to intercept and fake an iPhone reboot: We’ll dissect the iOS system and show how it’s possible to alter a shutdown event, tricking a user that got infected into thinking that the phone has been powered off, but in fact, it’s still running. The “NoReboot” approach simulates a real shutdown.





































Let's personalize your content