GUEST ESSAY: NewsCorp hack shows cyber espionage, squelching of press freedom on the rise
The Last Watchdog
APRIL 5, 2022
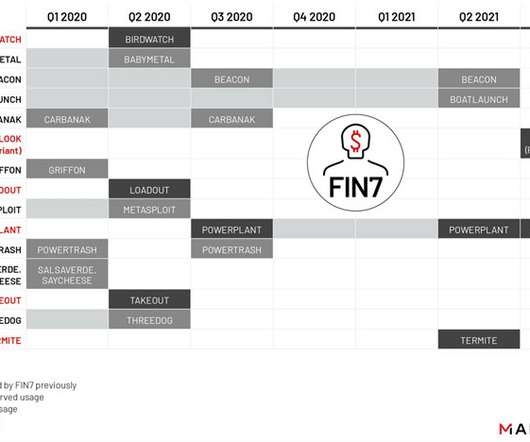
As the dust settles following the recently disclosed hack of NewsCorp , important lessons are emerging for the cybersecurity and journalism communities. Related: How China challenged Google in Operation Aurora. The Chinese government is well known for its censorship– and frequent harassment and intimidation of foreign journalists. These are the foremost reasons China is ranked fourth worst globally regarding press freedoms.







































Let's personalize your content