Hackers Using Fake Police Data Requests against Tech Companies
Schneier on Security
APRIL 5, 2022
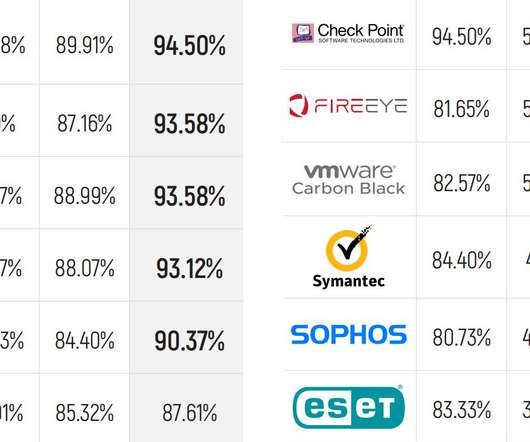
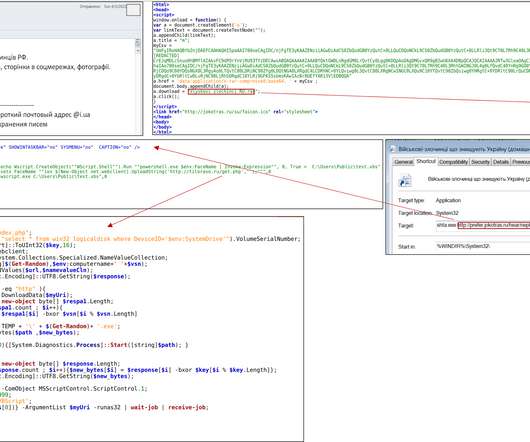
Brian Krebs has a detailed post about hackers using fake police data requests to trick companies into handing over data. Virtually all major technology companies serving large numbers of users online have departments that routinely review and process such requests, which are typically granted as long as the proper documents are provided and the request appears to come from an email address connected to an actual police department domain name.








































Let's personalize your content