ChatGPT Privacy Flaw
Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Lohrman on Security
MARCH 5, 2023
The White House released a new national cybersecurity strategy this past week with five pillars. What’s in the plan, and how will this impact public- and private-sector organizations?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
MARCH 17, 2023
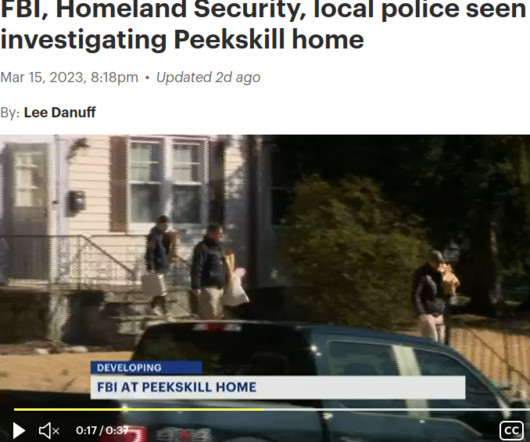
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums , a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forum’s administrator “ Pompompurin ” has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums , a remarkably similar crime forum that the FBI infiltrated and dismantled in 20

Tech Republic Security
MARCH 29, 2023
Learn how to protect your organization and users from this Android banking trojan. The post Nexus Android malware targets 450 financial applications appeared first on TechRepublic.

Speaker: Speakers:
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Bleeping Computer
MARCH 28, 2023
Cybersecurity researchers have discovered a fundamental security flaw in the design of the IEEE 802.11 WiFi protocol standard, allowing attackers to trick access points into leaking network frames in plaintext form. [.

We Live Security
MARCH 14, 2023
ESET Research uncovered a campaign by APT group Tick against a data-loss prevention company in East Asia and found a previously unreported tool used by the group The post The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia appeared first on WeLiveSecurity
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Lohrman on Security
MARCH 26, 2023
The world is buzzing about the new AI applications that are rapidly changing the landscape at home and work. But what about copyright protections, artistry and even fake news as our AI journey accelerates?

Krebs on Security
MARCH 20, 2023
A new breach involving data from nine million AT&T customers is a fresh reminder that your mobile provider likely collects and shares a great deal of information about where you go and what you do with your mobile device — unless and until you affirmatively opt out of this data collection. Here’s a primer on why you might want to do that, and how.

Tech Republic Security
MARCH 30, 2023
The new AI security tool, which can answer questions about vulnerabilities and reverse-engineer problems, is now in preview. The post Microsoft adds GPT-4 to its defensive suite in Security Copilot appeared first on TechRepublic.

Bleeping Computer
MARCH 25, 2023
American university researchers have developed a novel attack which they named "Near-Ultrasound Inaudible Trojan" (NUIT) that can launch silent attacks against devices powered by voice assistants, like smartphones, smart speakers, and other IoTs. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Dark Reading
MARCH 7, 2023
More than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information.

Security Boulevard
MARCH 29, 2023
Skyhawk Security today revealed it is employing ChatGPT to add generative artificial intelligence (AI) capabilities to its cloud threat detection and response (CDR) platform at no extra charge. Skyhawk Security CEO Chen Burshan said in addition to providing textual explanations of the evolution of a security incident discovered by the company’s platform, ChatGPT also makes.

CyberSecurity Insiders
MARCH 22, 2023
Cybercriminals are smarter, faster, and more relentless in their attacks than in times past. Data breaches are a serious threat to organizations, but vulnerability management automation can help reduce the number of incidents businesses face each year. Managing vulnerabilities is difficult in an increasingly connected cyber environment. Companies have their own networks, networks connected to their supply chains, vendor access, remote workers, and other entry points, all creating security gaps.

CSO Magazine
MARCH 20, 2023
The emergence of effective natural language processing tools such as ChatGPT means it's time to begin understanding how to harden against AI-enabled cyberattacks. The natural language generation capabilities of large language models (LLMs) are a natural fit for one of cybercrime’s most important attack vectors: phishing. Phishing relies on fooling people and the ability to generate effective language and other content at scale is a major tool in the hacker’s kit.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
MARCH 23, 2023
Microsoft has already seen millions of phishing emails sent every day by attackers using this phishing kit. Learn how to protect your business from this AitM campaign. The post Massive adversary-in-the-middle phishing campaign bypasses MFA and mimics Microsoft Office appeared first on TechRepublic.

Bleeping Computer
MARCH 29, 2023
A digitally signed and trojanized version of the 3CX Voice Over Internet Protocol (VOIP) desktop client is reportedly being used to target the company's customers in an ongoing supply chain attack. [.

Graham Cluley
MARCH 17, 2023
Well, this isn’t good. Google has issued a warning that some Android phones can be hacked remotely, without the intended victim having to click on anything.

Security Boulevard
MARCH 30, 2023
UK National Crime Agency nips it in the bud: Aims to scare straight naughty DDoS kiddies. The post Brits Slap Wrists of DDoS Kids, via NCA’s Fake Booter Sites appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

CyberSecurity Insiders
MARCH 19, 2023
After the release of ChatGPT in November 2022, the OpenAI CEO and the people behind the conversational chatbot launch say that they are equally scared of the negative consequences that the newly developed technology can fetch in the future. Sam Altman, the tech brain leading the company, now owned by Microsoft, spoke a few words about what the world was intending to say about the tech.
Dark Reading
MARCH 24, 2023
In two days, ethical researchers from 10 countries have unearthed more than 22 zero-day bugs in a wide range of technologies at the annual hacking contest.

Tech Republic Security
MARCH 24, 2023
Cisco’s just-released 2023 Cybersecurity Index shows companies will invest more in security, but the solution may be a larger tent, not more umbrellas. The post Even after armed with defense tools, CISOs say successful cyberattacks are ‘inevitable’: New study appeared first on TechRepublic.

Bleeping Computer
MARCH 31, 2023
A 10-year-old Windows vulnerability is still being exploited in attacks to make it appear that executables are legitimately signed, with the fix from Microsoft still "opt-in" after all these years. Even worse, the fix is removed after upgrading to Windows 11. [.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CSO Magazine
MARCH 23, 2023
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued advisories on 49 vulnerabilities in eight industrial control systems (ICS) this week, which are used across multiple critical infrastructure sectors. The vulnerabilities identified by CISA were tracked in products from ICS providers including Siemens, Hitachi, Rockwell, Delta Electronics, VISAM, and Keysight.

Security Boulevard
MARCH 16, 2023
Ben is disappointed: FBI reports huge rise in cryptocurrency investment scams. Why am I not surprised? The post Scams Lost US $10 BILLION in 2022 — Crypto Fraud Grows Fast appeared first on Security Boulevard.

CyberSecurity Insiders
MARCH 9, 2023
Traditional vulnerability management is in need of a desperate change due to the lack of effectiveness in combating modern cyberattacks. It’s a bold statement, but true, nonetheless, because it’s just not enough. Numbers don’t lie, and the only direction the average cost of recovering from cyberattacks seems to move is up. Putting the monetary effect aside, a successful cyberattack from ineffective vulnerability management can fatally hit an organization’s reputation.

WIRED Threat Level
MARCH 26, 2023
The GOP-fueled far right differs from similar movements around the globe, thanks to the country’s politics, electoral system, and changing demographics.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Tech Republic Security
MARCH 15, 2023
AI-generated phishing emails, including ones created by ChatGPT, present a potential new threat for security professionals, says Hoxhunt. The post Humans are still better at creating phishing emails than AI — for now appeared first on TechRepublic.

Bleeping Computer
MARCH 27, 2023
Microsoft is introducing a new Exchange Online security feature that will automatically start throttling and eventually block all emails sent from "persistently vulnerable Exchange servers" 90 days after the admins are pinged to secure them. [.

Graham Cluley
MARCH 9, 2023
The US Transportation and Security Administration (TSA) has issued new requirements for airport and aircraft operators who, they say, are facing a "persistent cybersecurity threat." Read more in my article on the Tripwire State of Security blog.

Security Boulevard
MARCH 3, 2023
The vast majority—92% of companies across all verticals, states and business sizes—are still unprepared for compliance with the California Consumer Privacy Act (CCPA) and California Privacy Rights Act (CPRA), while a similar percentage (91%) are unprepared for GDPR compliance. A report from Cytrio revealed these organizations are still using time-consuming and error-prone manual processes to.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content