Joker malware still able to bypass Google Play Store checks
Security Affairs
FEBRUARY 22, 2020
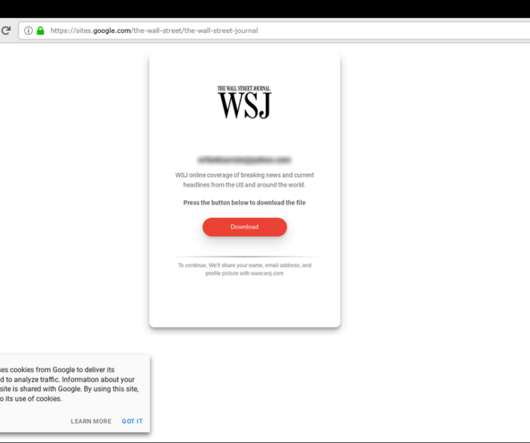
Once the malware has checked the region of the target device, it will contact the C2 server to load a configuration file containing a URL for another payload that is downloaded and executed. The subscription process is totally invisible to the user because the URLs for the premium services are opened in a hidden webview.














Let's personalize your content