Infographic: The 5 phases of a ransomware attack
Tech Republic Security
JULY 28, 2016
How to defend against attackers and avoid ransom demands.

Tech Republic Security
JULY 28, 2016
How to defend against attackers and avoid ransom demands.

Elie
JULY 11, 2016
Here are the 5 ways I bulletproof my credit cards against identity theft, and you can use them yourself very easily. As a bonus, at the end of the post I have added an experimental step to defend against the recent chip downgrading attack.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

ForAllSecure
JULY 26, 2016
By David Brumley. In 2008 I started as a new assistant professor at CMU. I sat down, thought hard about what I had learned from graduate school, and tried to figure out what to do next. My advisor in graduate school was Dawn Song , one of the top scholars in computer security. She would go on to win a MacArthur "Genius" Award in 2010. She's a hard act to follow.

Kali Linux
JULY 19, 2016
Kali Linux Dojo, BlackHat 2016 - Las Vegas We have really enjoyed doing the Dojo at Black Hat the last few years. It’s been a great opportunity to show off some of the lesser known (but oh so useful) features of Kali Linux as well as interact with the user base. But one of the limitations of the previous structure was that while this was a hands-on exercise, many attendees moved at different paces from each other.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
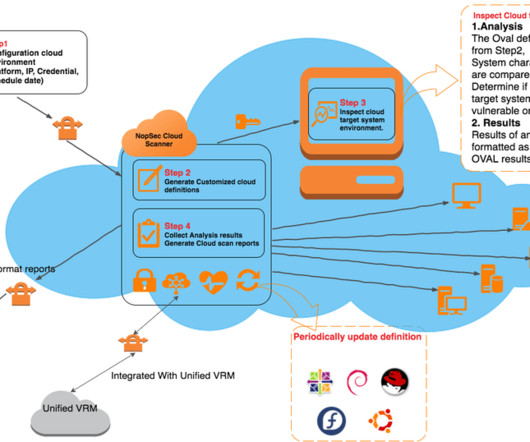
NopSec
JULY 13, 2016
Most organizations are currently migrating their computing infrastructure into the public cloud (AWS, Google, Azure) usually embracing a mixed private / public cloud model. Most SaaS solutions, including NopSec, already base their entire computing infrastructure on public clouds. This creates a unique challenge in terms of setting up proper vulnerability management processes to address the cloud environment’s peculiarities.

Privacy and Cybersecurity Law
JULY 27, 2016
The Canadian Radio-television and Telecommunications Commission (CRTC) issued an enforcement advisory to both businesses and individuals that send commercial electronic […].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Spinone
JULY 8, 2016
Let’s explore how to avoid ransomware in Google Workspace. Ransomware has been a consistent threat to your cloud security. It can corrupt your computer files and files you store with the cloud service providers. There are many ways to spread such malware. How G Suite Ransomware May Spread Emails are frequently used way. You receive […] The post How to Avoid Ransomware in Google Workspace?

ForAllSecure
JULY 16, 2016
In 2008 I started as a new assistant professor at CMU. I sat down, thought hard about what I had learned from graduate school, and tried to figure out what to do next. My advisor in graduate school was Dawn Song , one of the top scholars in computer security. She would go on to win a MacArthur "Genius" Award in 2010. She's a hard act to follow. I was constantly reminded of this because, by some weird twist of fate, I was given her office when she moved from CMU to Berkeley.

Kali Linux
JULY 10, 2016
The folks at Black Hat have been kind enough to invite us once again to deliver a Kali Dojo in Las Vegas this year. The event will be held on the 4th of August at the Mandalay Bay hotel, and will be open to all Black Hat pass types. This year our Dojo will be set up differently, allowing for a larger crowd and much more interaction. We are going to hold a full day event, featuring several main activity areas : Area 1: Customising Kali ISOs using live-build One to the most important aspects of Ka

NopSec
JULY 6, 2016
NopSec released a featured annual report, “2016 State of Vulnerability Risk Management.” The report reveals key security threats by industry, cross-industry remediation developments, malware-based vulnerabilities, and the rising correlation of social media and security threats. Conducted by the NopSec Labs research team, the report analyzes over a million unique vulnerabilities and more than 76,000 vulnerabilities contained in the National Vulnerability Database over a 20-year period.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Privacy and Cybersecurity Law
JULY 13, 2016
The European Commission yesterday issued an adequacy decision adopting the EU-US Privacy Shield, which replaces Safe Harbor as a framework […].

Tech Republic Security
JULY 11, 2016
Is your business data on the Dark Web? Learn how to find out if you've been compromised in this step-by-step guide to accessing the underbelly of the internet.

Spinone
JULY 8, 2016
Let’s explore how to avoid Ransomware viruses, that are a new very serious threat to your cloud security that can corrupt your computer files and files you store with the cloud service providers. There are many ways to spread such viruses. How G Suite Ransomware May Spread Emails are frequently used way. You receive a message like “I Love You”, then click a link with a virus, and you are done.

ForAllSecure
JULY 16, 2016
In 2008 I started as a new assistant professor at CMU. I sat down, thought hard about what I had learned from graduate school, and tried to figure out what to do next. My advisor in graduate school was Dawn Song , one of the top scholars in computer security. She would go on to win a MacArthur "Genius" Award in 2010. She's a hard act to follow. I was constantly reminded of this because, by some weird twist of fate, I was given her office when she moved from CMU to Berkeley.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
JULY 25, 2016
Zero Days is a documentary by Oscar-winning filmmaker Alex Gibney about the cyberwarfare Pandora's Box that was opened with the Stuxnet malware. Find out why Jack Wallen highly recommends the film.

Tech Republic Security
JULY 6, 2016
Linux Mint 18 brings version 3.0 of the Cinnamon desktop, and major architectural changes intended to harden the security of the popular distribution. But, some challenges remain.

Tech Republic Security
JULY 28, 2016
To encrypt email and files, you need to know how to work with PGP keys. Get up to speed on generating, exporting, and importing encryption keys with GnuPG.

Tech Republic Security
JULY 27, 2016
US President Barack Obama recently published a policy directive for cyber incident coordination, which outlines how the government should respond to cybersecurity attacks.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
JULY 26, 2016
As ransomware increasingly targets healthcare organizations, schools and government agencies, security experts offer advice to help IT leaders prepare and protect.

Tech Republic Security
JULY 25, 2016
The profits from ransomware are making it one of the fastest growing types of malware and new versions could negatively impact entire industries, according to a Cisco report.

Tech Republic Security
JULY 29, 2016
A 2-day mini-conference called TiaraCon aims to connect women interested in the cybersecurity field with job contacts and mentoring to create more inclusive work environments.

Tech Republic Security
JULY 14, 2016
Microsoft recently won an appeal over a US search warrant that aimed to force the company to turn over data that was stored on foreign servers.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
JULY 13, 2016
Encrypting your email is a great step towards more secure communication. Gmail, Mailvelope, and Virtru can help streamline your encrypted email efforts.

Tech Republic Security
JULY 13, 2016
Documentary filmmaker Yuval Orr interviewed cryptoanarchists, hackers, and security experts about why encryption and privacy are important. His new movie will make you see the Dark Web in a new light.

Tech Republic Security
JULY 12, 2016
Computer scientists enhance data security by simplifying the creation of truly random numbers used to build encryption keys.

Tech Republic Security
JULY 12, 2016
Analytics managers need to do two things to protect IoT-generated data from an often-overlooked threat.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
JULY 28, 2016
There are a plethora of IoT-connected devices that create a huge security risk for companies, whether at the corporate office, or at an employee's home office.

Tech Republic Security
JULY 29, 2016
Everyone from famed hacker Kevin Mitnick to the IEEE Computer Society agree that a little end user training goes a long way in preventing phishing attacks.

Tech Republic Security
JULY 8, 2016
In a recent privacy push, Facebook announced that it was rolling out the beta of a new feature called 'secret conversations,' bringing better encryption and ephemeral messaging.

Tech Republic Security
JULY 5, 2016
A new malware called HummingBad, associated with Chinese cyber criminals Yingmob, has infected millions of devices and brings in millions of dollars of fake ad revenue.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.
Let's personalize your content