IoT, encryption, and AI lead top security trends for 2017
Tech Republic Security
APRIL 26, 2017
A new Forrester report identified the top 14 cybersecurity trends for enterprises to watch in 2017.

Tech Republic Security
APRIL 26, 2017
A new Forrester report identified the top 14 cybersecurity trends for enterprises to watch in 2017.
Kali Linux
APRIL 24, 2017
Finally, it’s here! We’re happy to announce the availability of the Kali Linux 2017.1 rolling release , which brings with it a bunch of exciting updates and features. As with all new releases, you have the common denominator of updated packages , an updated kernel that provides more and better hardware support, as well as a slew of updated tools - but this release has a few more surprises up its sleeve.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Privacy and Cybersecurity Law
APRIL 28, 2017
On April 4, 2017, Tennessee Governor Bill Haslam signed into law an amendment to the state’s data breach notification law, making two […].
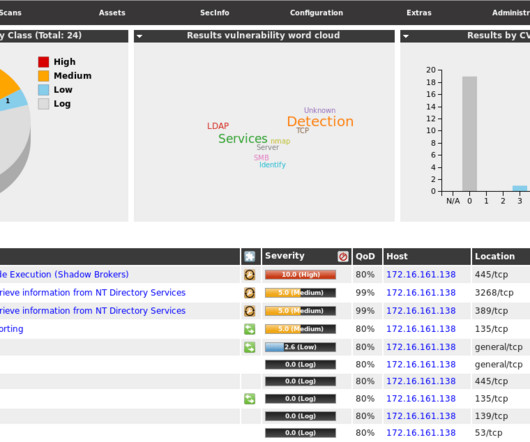
NopSec
APRIL 26, 2017
According to the The Register’s article , last week we started assisting to the widespread exploitation of The Shadow Brokers ’ leaked Windows exploits, compromising thousands of vulnerable hosts over the Internet. This widespread exploitation prompted me to release this blog post that I have been mulling for a while. As part of the Equation Group’s hacking tools stash, leaked last week by The Shadow Brokers group, this is the latest installment of several leaks featuring network devices vuln

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
APRIL 28, 2017
A report from IBM Security revealed a 937% increase in records stolen from the financial sector in 2016. Here's what you need to know and do to protect your sensitive data.

Kali Linux
APRIL 23, 2017
A couple of weeks back we added more HTTPS support to our Kali infrastructure, and wanted to give our users some guidance and point out what’s new. While our Kali Linux download page (and shasums) has always been served via HTTPS, our mirror redirector has not. Now that we generate weekly images, secure access to the mirror redirector has become crucial.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
APRIL 24, 2017
According to a global survey from the Centre for International Governance Innovation, almost half of all respondents say they don't trust online shopping.

Tech Republic Security
APRIL 27, 2017
The Evolution of Security Skills, a new report from CompTIA, is calling on IT security professionals to form a more proactive strategy and examine emerging threats.

Tech Republic Security
APRIL 27, 2017
According to Verizon's 2017 Data Breach Investigations Report, espionage-related attacks are growing in popularity, with malware and phishing still go-to tools for hackers as well.

Tech Republic Security
APRIL 28, 2017
The new STEAM-Con Connection offers cybersecurity vendors an alternative to staffing trade show booths with models. Here's how it works.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
APRIL 27, 2017
Android security doesn't have to be a challenge. Here are a few simple and quick ways to make ensure your device is secure.

Tech Republic Security
APRIL 25, 2017
Antivirus provider Webroot recently pushed an updated causing it to read Windows system files as malware and label Facebook a phishing site.

Tech Republic Security
APRIL 25, 2017
AV-TEST engineers don't think all data protection and backup software is quite ready for prime time. Find out which product received AV-TEST's Approved Backup & Data Security Software certificate.

Tech Republic Security
APRIL 25, 2017
Forrester just released a list of the top cybersecurity trends for 2017. Here are the top three.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
APRIL 26, 2017
Patching critical vulnerabilities requires both technological and human-oriented solutions. Learn some techniques for maximizing user compliance.

Tech Republic Security
APRIL 28, 2017
The National Security Agency will stop collecting Americans' emails and texts to people from other countries, and/or those that mention someone who is currently under surveillance.

Tech Republic Security
APRIL 24, 2017
See how cybercriminals craft collective attention threats--and how university researchers plan to get the word out before attacks start.

Tech Republic Security
APRIL 28, 2017
Open wifi networks can compromise your data, and international customs might lead to a cyber-breach. iJET CEO Bruce McIndoe explains the best ways to take technological precautions while traveling.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
APRIL 25, 2017
Malvertising grew by 132% last year. Learn how persistent threat monitoring tools protect companies from cross-site scripting vulnerabilities.

Tech Republic Security
APRIL 27, 2017
Cyberattacks on financial institutions skyrocketed in 2016. So where are the threats coming from?
Let's personalize your content