Three Top Russian Cybercrime Forums Hacked
Krebs on Security
MARCH 4, 2021
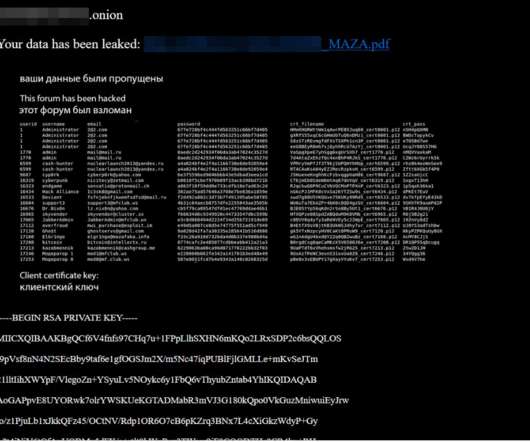
Over the past few weeks, three of the longest running and most venerated Russian-language online forums serving thousands of experienced cybercriminals have been hacked. In two of the intrusions, the attackers made off with the forums’ user databases, including email and Internet addresses and hashed passwords. Members of all three forums are worried the incidents could serve as a virtual Rosetta Stone for connecting the real-life identities of the same users across multiple crime forums.







































Let's personalize your content